Windows Enumeration
if you are interested in network penetration tester or red teaming I collected most of the commands used in windows enumeration,enjoy
Operating System
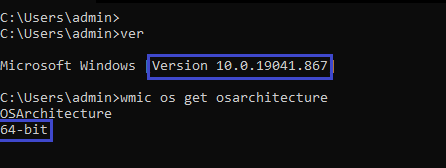
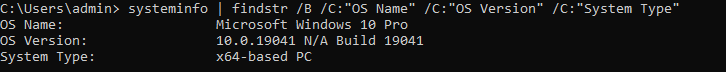
What version of windows is running? Is it 32 or 64-bit?
ver
wmic os get osarchitecture
os version
systeminfo | findstr /B /C:"OS Name" /C:"OS Version" /C:"System Type"
Hostname
Hostname prints the name of the PC you are currently connected to.
whoami:tells you the domain and the username of the user currently connected as
hostname
whoami
set computername
Network
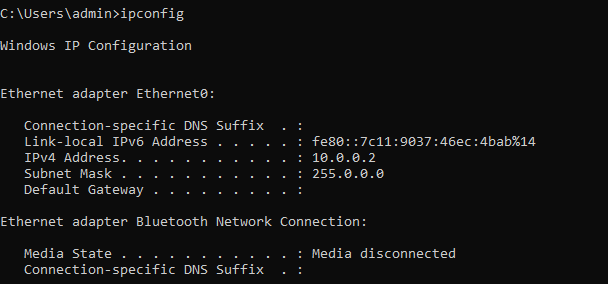
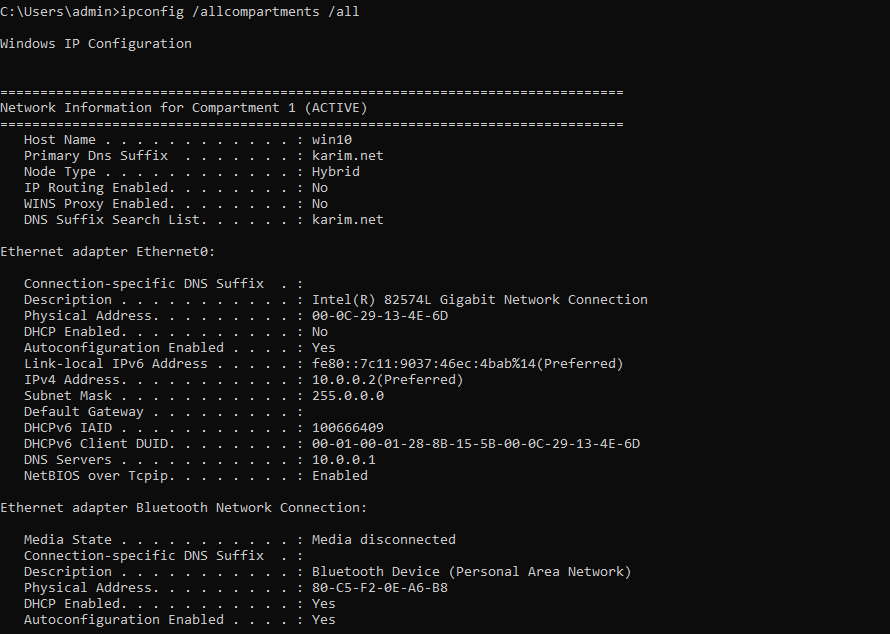
Ipconfig displays all the networking information of the current PC your connected to.
ipconfig
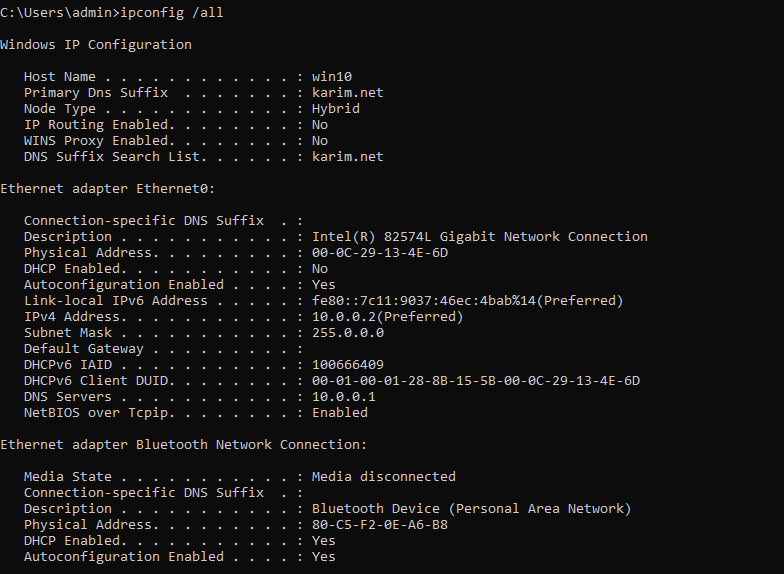
If you add a /all to the ipconfig command it will give you a more detailed output which includes the DHCP and DNS server that the PC is connected to.
ipconfig /all
ipconfig /allcompartments /all
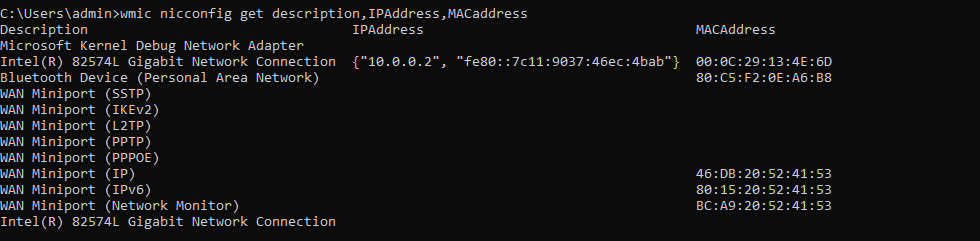
wmic nicconfig get description,IPAddress,MACaddress
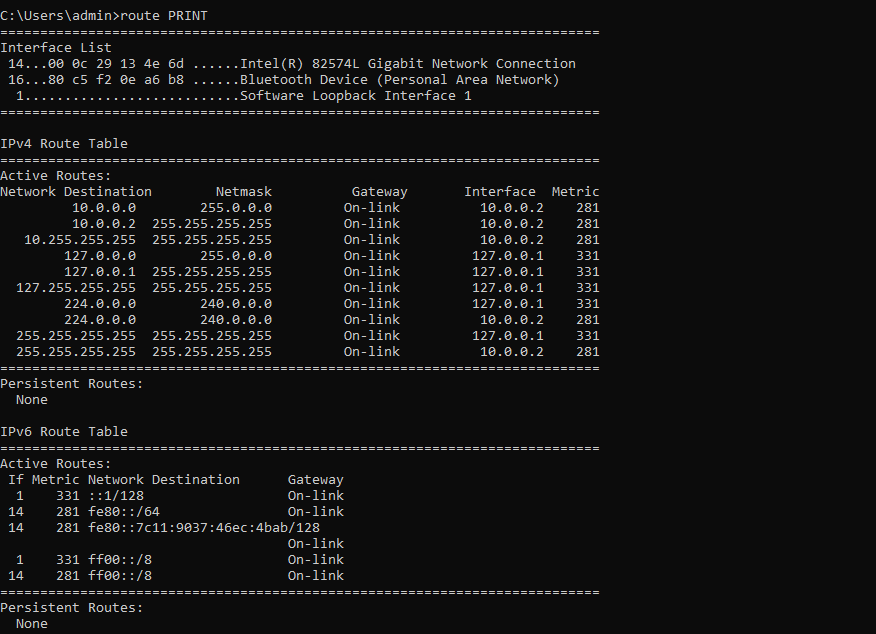
route print command displays the routing table of the current windows PC your connected to
route PRINT
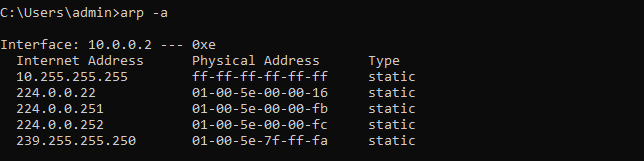
The arp -a command displays the IP to physical address translation used by the address resolution protocol.
arp -a
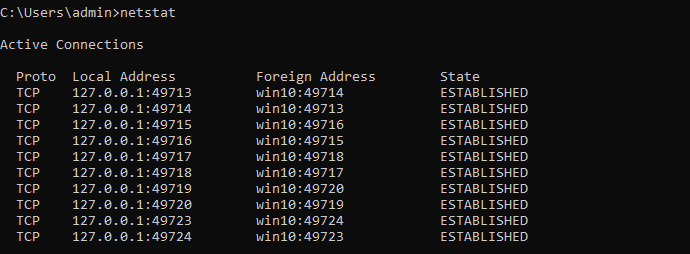
netstat is a command-line network utility that displays network connections for Transmission Control Protocol, routing tables, and a number of network interface and network protocol
netstat
netstat -ano
firewall configuration
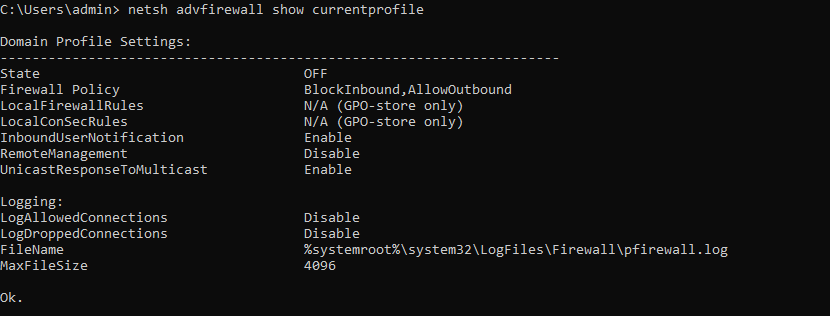
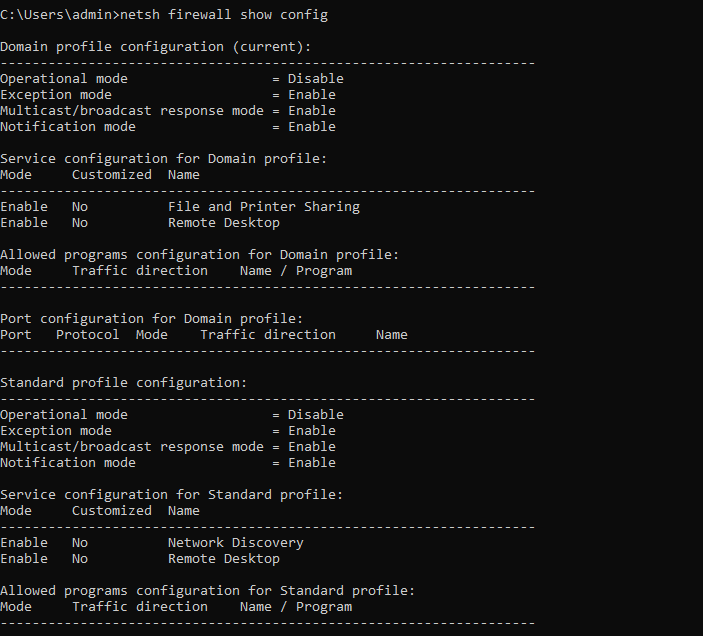
netsh firewall gives you options to control the windows firewall
netsh advfirewall show currentprofile
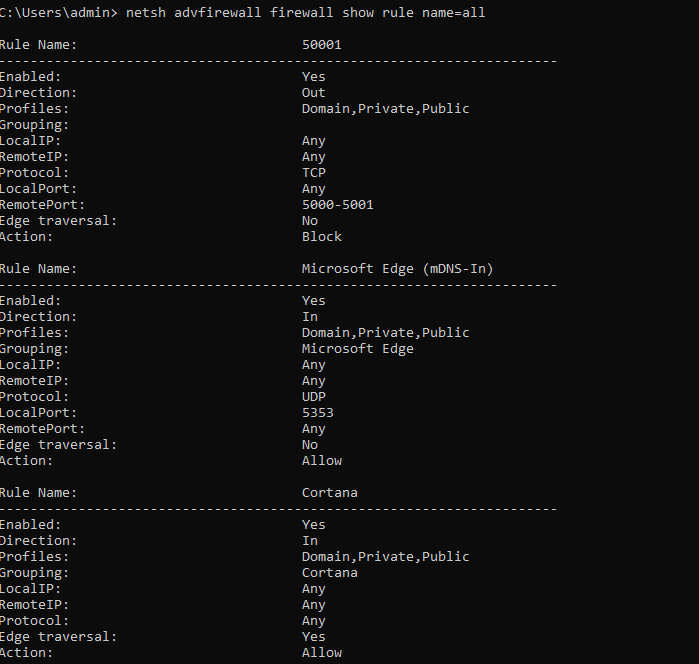
netsh advfirewall firewall show rule name=all
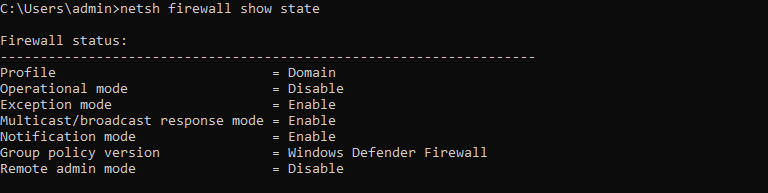
netsh firewall show state
netsh firewall show config
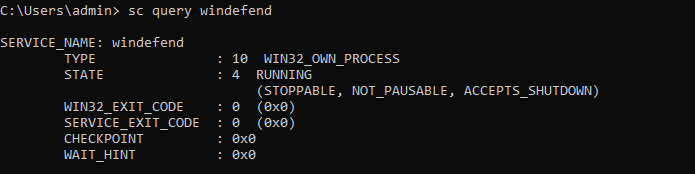
windows defender
sc query windefend
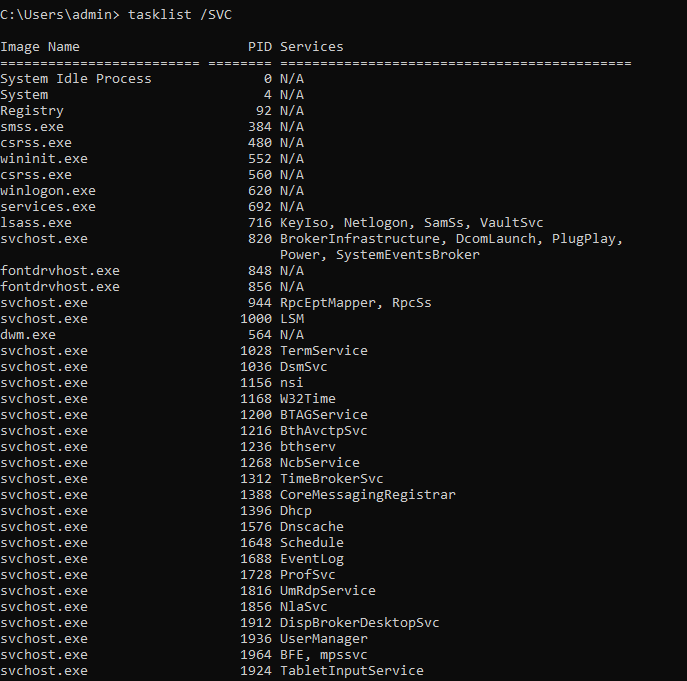
running processes
Tasklist displays a list of currently running processes on a PC.
tasklist /SVC
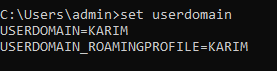
Is the machine on a domain?
set userdomain
Registry
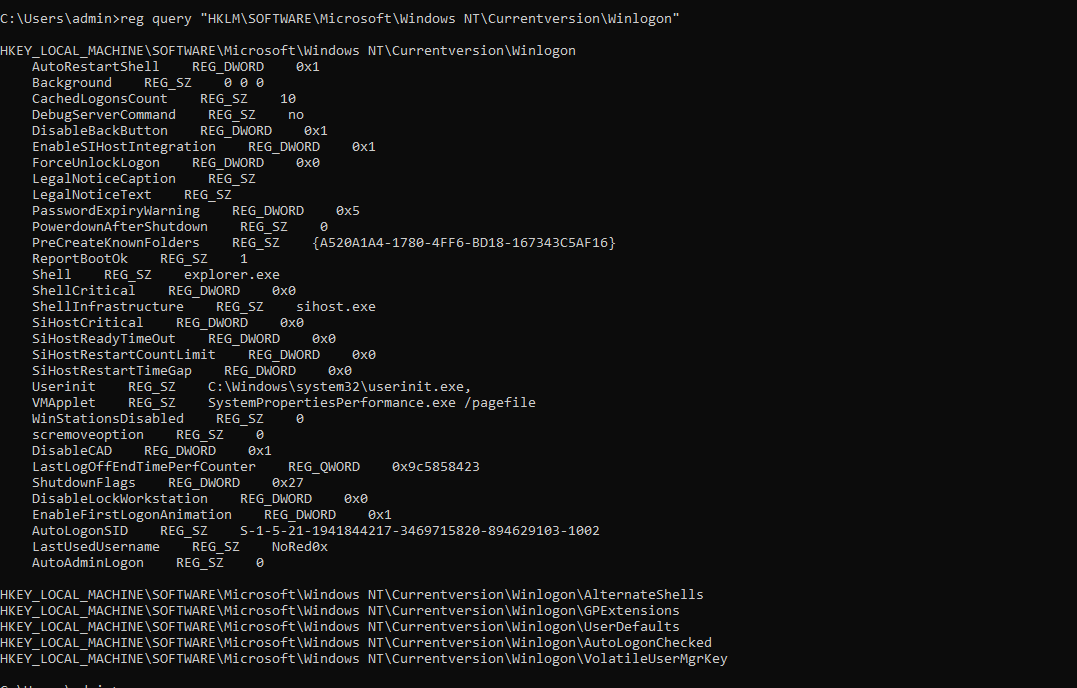
Windows autologin
reg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon"
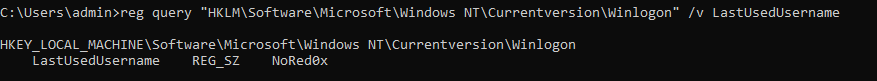
reg query "HKLM\Software\Microsoft\Windows NT\Currentversion\Winlogon" /v LastUsedUsername
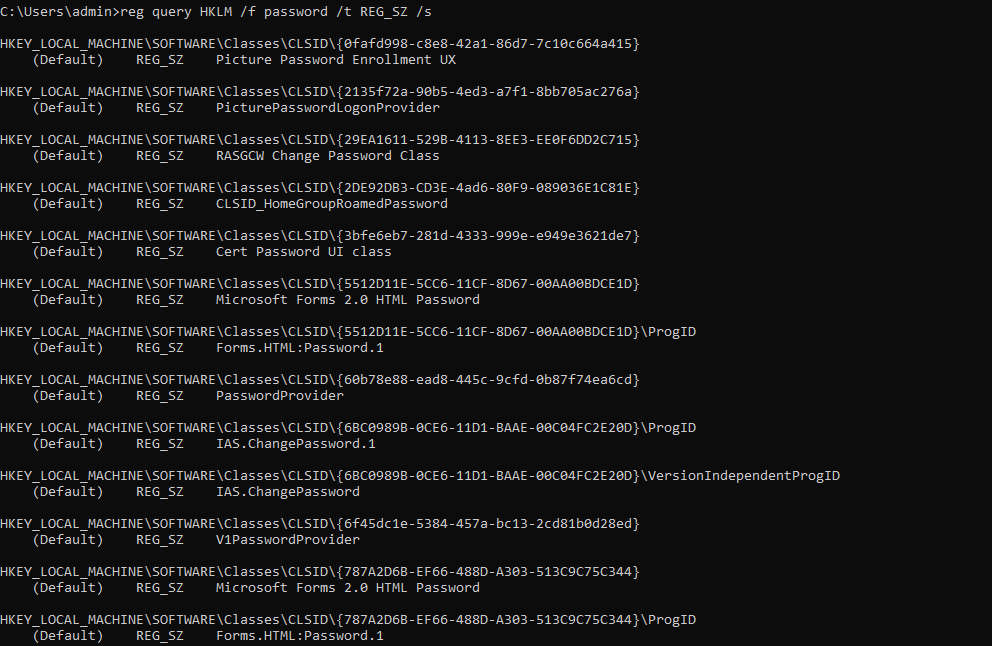
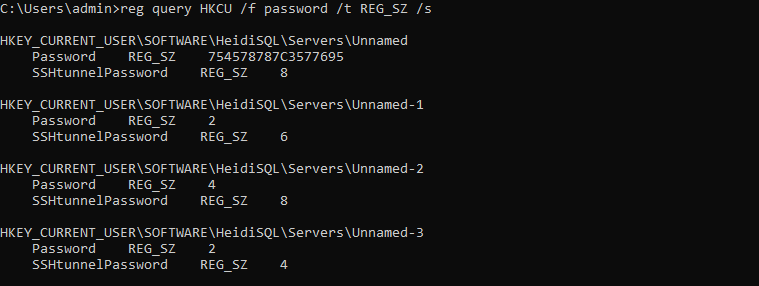
Search for password in registry
reg query HKLM /f password /t REG_SZ /s
reg query HKCU /f password /t REG_SZ /s
Hardware Information
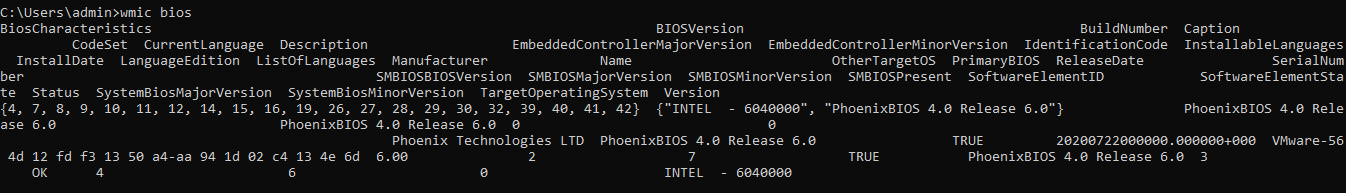
wmic bios
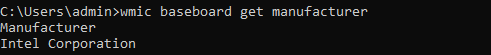
wmic baseboard get manufacturer
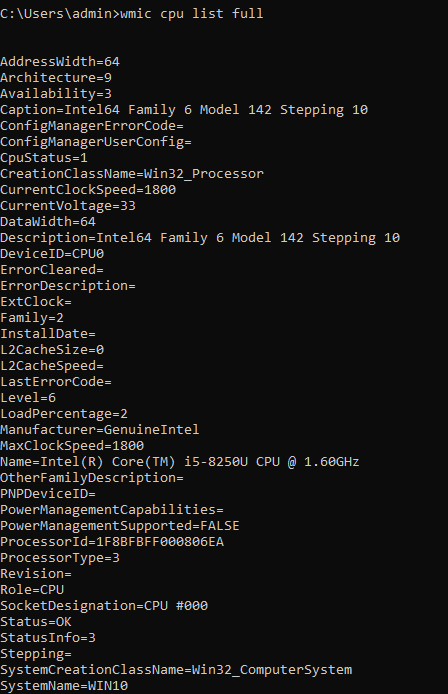
wmic cpu list full
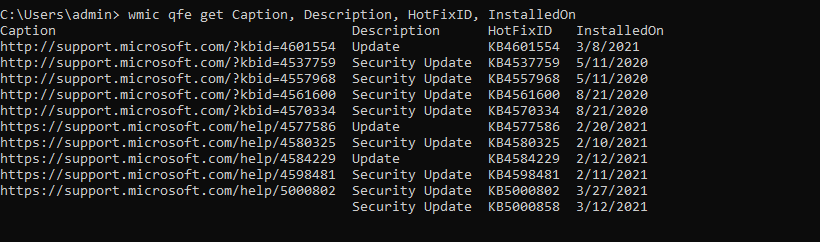
patches are installed
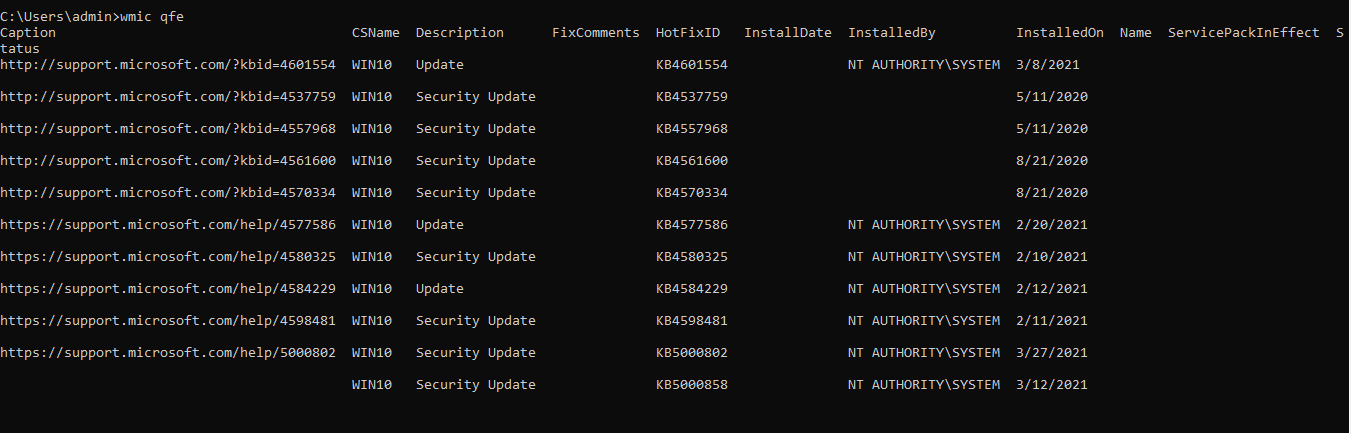
qfe to the wmic command you get a list of all the installed hotfixes installed on a windows PC. What patches are installed?
wmic qfe
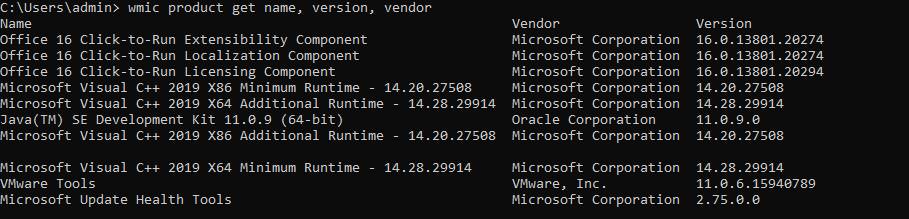
install app
wmic product get name, version, vendor
wmic qfe get Caption, Description, HotFixID, InstalledOn
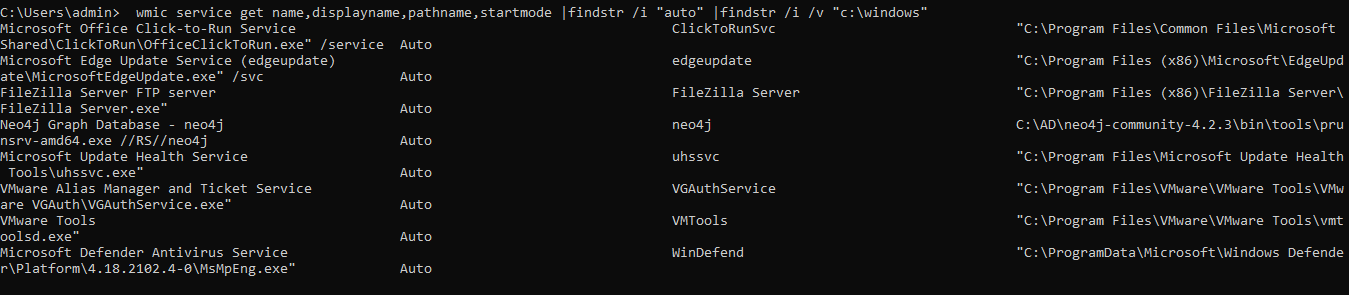
wmic service get name,displayname,pathname,startmode |findstr /i "auto" |findstr /i /v "c:\windows"
Unquoted Service Paths
Find Services With Unquoted Paths
wmic service get name,displayname,pathname,startmode |findstr /i "auto" |findstr /i /v "c:\windows\\" |findstr /i /v """
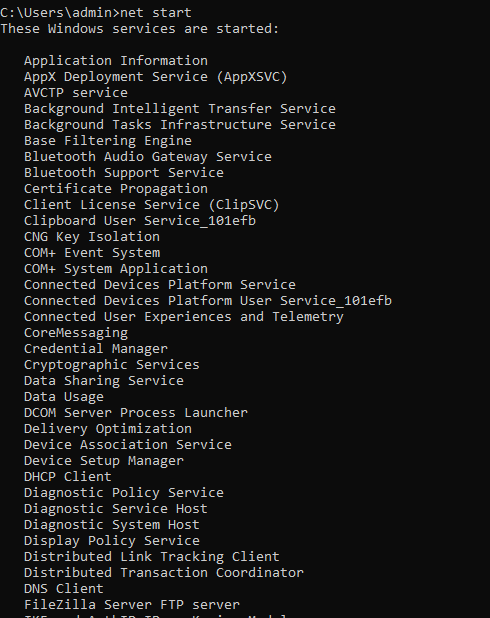
Net Start
allows you to manage services running on the PC
net start
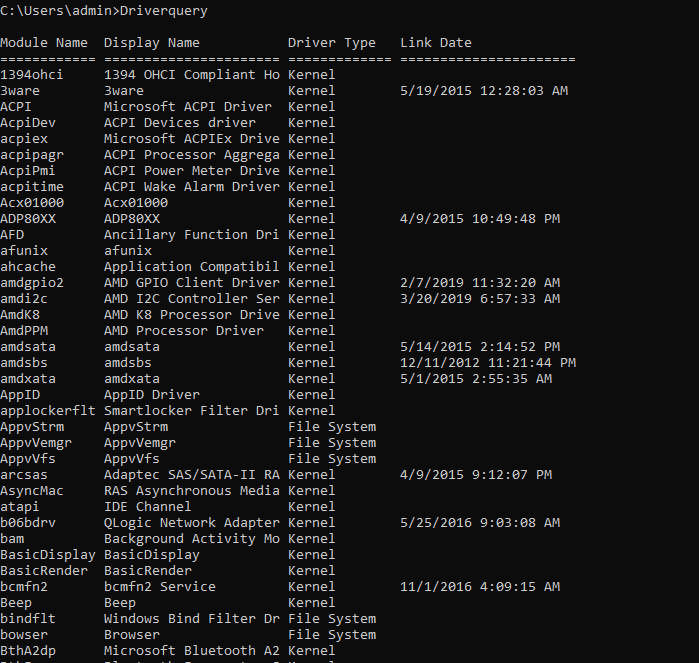
device drivers
Driverquery quickly displays all the device drivers of the Pc your connected to.
Driverquery
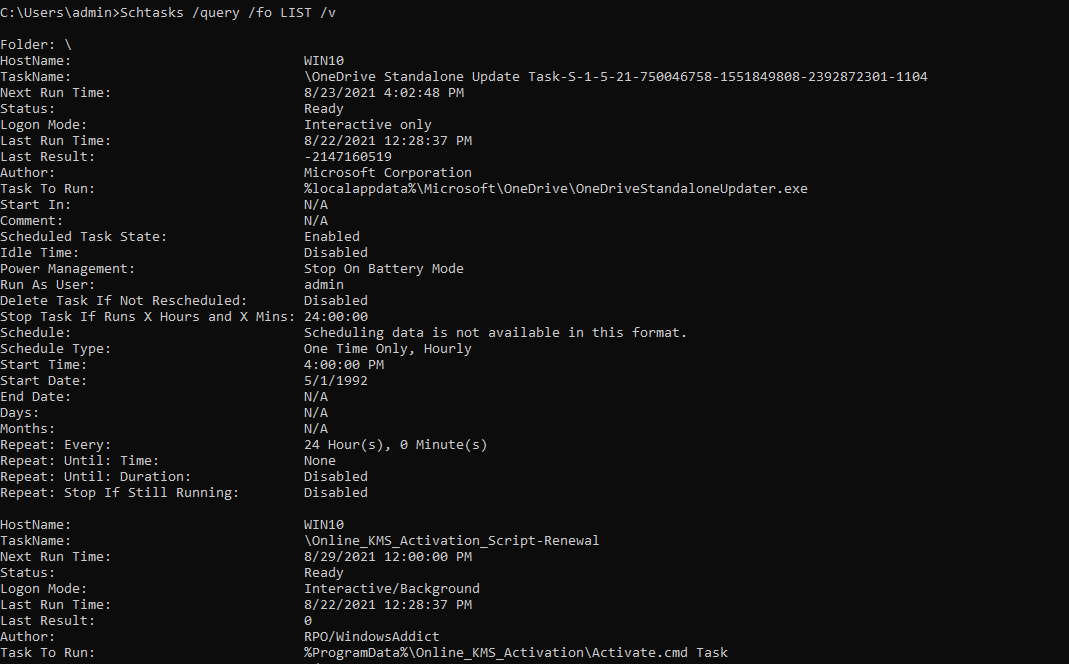
scheduled tasks
Schtasks allows you to manage scheduled tasks running on a local or remote machine
Schtasks /query /fo LIST /v
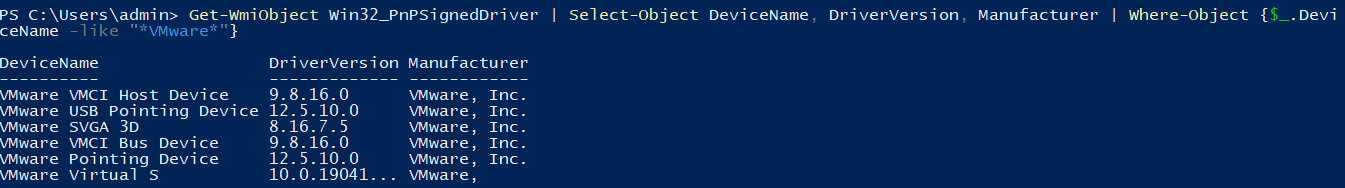
device&kernal
Get-WmiObject Win32_PnPSignedDriver | Select-Object DeviceName, DriverVersion, Manufacturer | Where-Object {$_.DeviceName -like "*VMware*"}
Search for Cleartext Passwords
findstr /si password *.txt
findstr /si password *.xml
findstr /si password *.ini
Find all those strings in config files.
dir /s *pass* == *cred* == *vnc* == *.config*
Find all passwords in all files.
findstr /spin "password" *.*
findstr /spin "password" *.*
I finished this part about windows enumeration today waiting me in the next part.