Active Directory Domain Trust and forest Enumeration Part-3 With Powerview
Overview
Active Directory follows a clear hierarchy, from top to bottom. In that hierarchy are: forests, trees, and domains.
- Forests:represent the complete Active Directory instance, and are logical containers made up of domain trees, domains, and organizational units.
- Trees:are collections of domains within the same DNS namespace; these include child domains.
- Domains:are logical groupings of network objects such as computers, users, applications, and devices on the network such as printers.
Active Directory trust
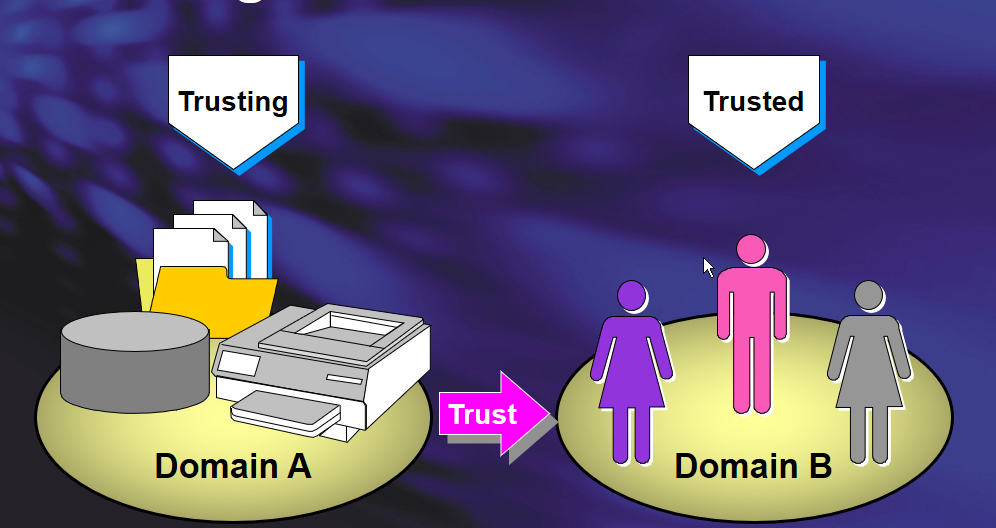
trust is a relationship between two domains or forests which allows users of one domain or forest to access resources in the other domain or forest
In simplest terms, it is the process of extending the security boundary of an AD domain or forest to include another AD domain or forest.
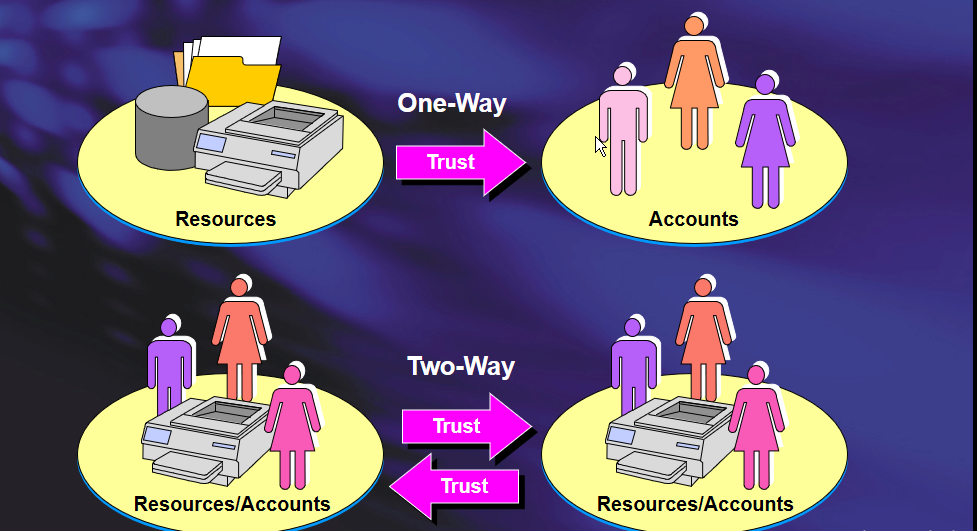
Trust Direction
- One-way trust(Unidirectional):Users in the trusted domain can access resources in the trusting domain but the reverse is not true.
- Two-way trust(Bidirectional):Users of both domains can access resources in the other domain
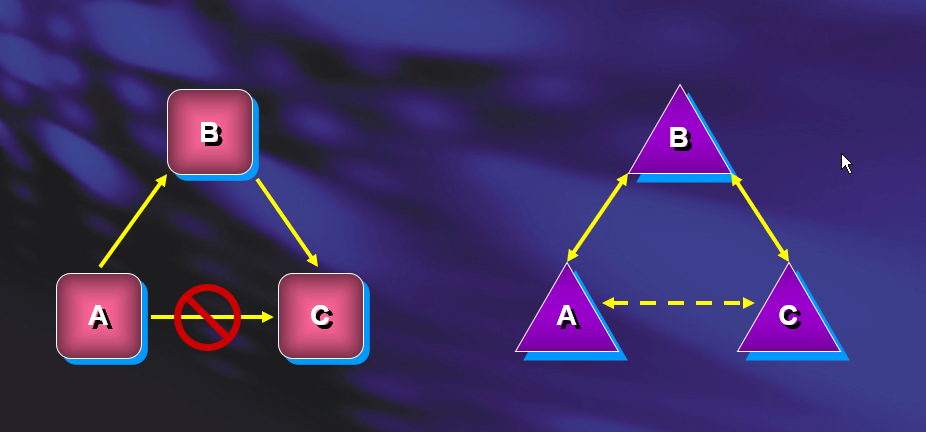
Trust Transitivity
Transitive
- Can be extended to establish trust relationships with other domains.
- All the default intra-forest trust relationships (Tree-root, Parent-Child) between domains within a same forest are transitive two-way trusts
Nontransitive
- Cannot be extended to other domains in the forest. Can be two-way or one-way.
- This is the default trust (called external trust) between two domains in different forests when forests do not have a trust relationship.
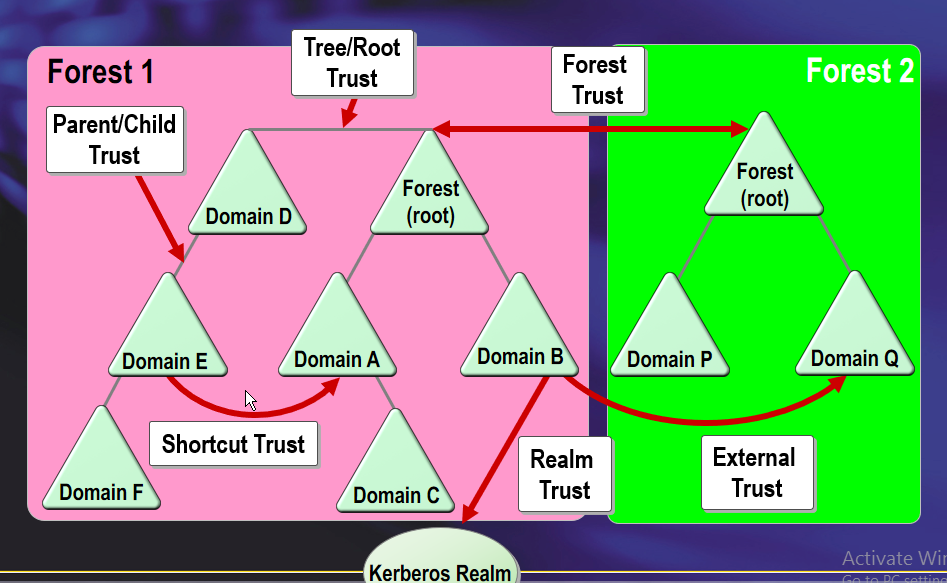
Relationship Trust
Parent/Child Trust
- A transitive, two-way parent-child trust relationship automatically created and establishes a relationship between a parent domain and a child domain whenever a new child domain is created using the AD DS installation process process within a domain tree.
- They can only exist between two domains in the same tree with the same contiguous namespace.
- The parent domain is always trusted by the child domain. You cannot manually create a Parent-Child trust.
Tree/Root Trust
- A transitive, two-way tree-root trust relationship automatically created and establishes a relationship between the forest root domain and a new tree, when you run the AD DS installation process to add a new tree to the forest.
- A tree-root trust can only be established between the roots of two trees in the same forest and are always transitive. You cannot manually create a tree-root trust
Shortcut Trust
- Shortcut trusts are manually created, one-way, transitive trusts.
- They can only exist within a forest.
- They are created to optimize the authentication process shortening the trust path.
- The trust path is the series of domain trust relationships that the authentication process must traverse between two domains in a forest that are not directly trusted by each other. Shortcut trusts shorten the trust path
Forest Trust
- Forest trusts are manually created, one-way transitive, or two-way transitive trusts that allow you to provide access to resources between multiple forests.
- Forest trusts uses both Kerberos v5 and NTLM authentication across forests where users can use their Universal Principal Name (UPN)
Realm Trust
- Trust Relationships with Other Operating Systems that also Support Kerberos Protocol
- One-Way Transitive or One-Way Non-Transitive Use Kerberos Authentication Only
- A Realm trust can be established to provide resource access and cross-platform inter-operability between an AD DS domain and non-Windows Kerberos v5 Realm.
External Trust
- An external trust is a one-way, non-transitive trust that is manually created to establish a trust relationship between AD DS domains that are in different forests, or between an AD DS domain and Windows NT 4.0 domain.
- External trusts allow you to provide users access to resources in a domain outside of the forest that is not already trusted by a Forest trust.
Get list of all domain trust for the currrent domain
Get-NetDomainTrust
Get-NetDomainTrust -Domain <domain>
Get-DomainTrustMapping
Forest
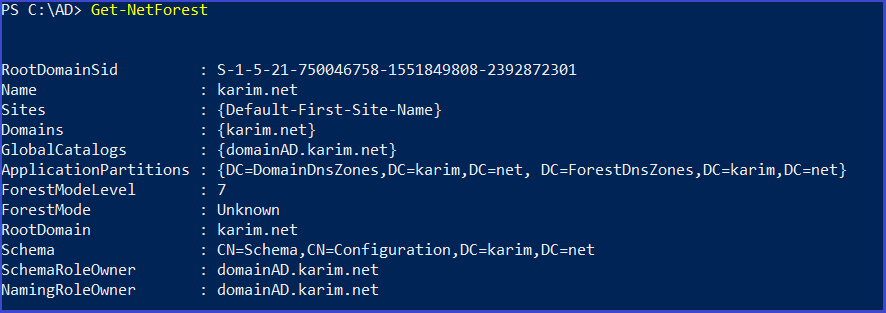
Get details about the current forest
Get-NetForest
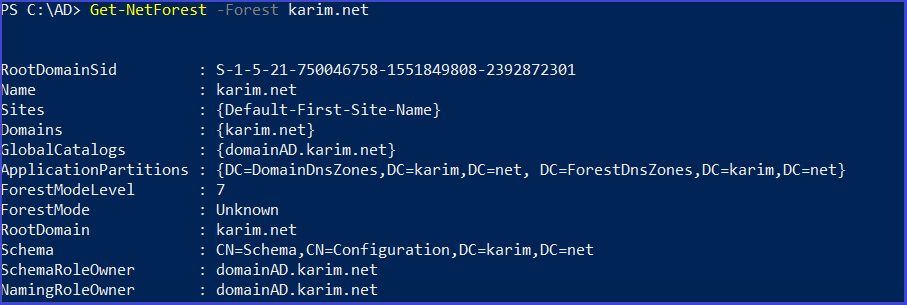
Get details about the other forest
Get-NetForest -Forest <forest>
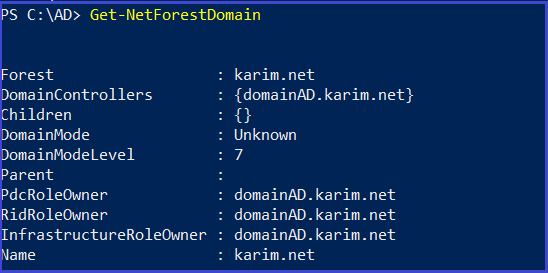
Get all domain in the current forest
Get-NetForestDomain
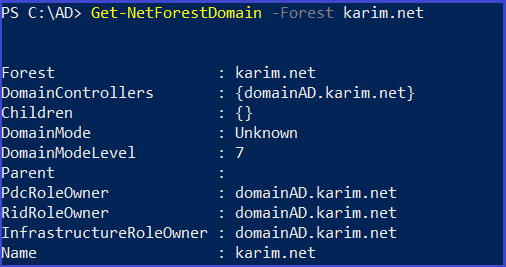
Get-NetForestDomain -Forest karim.net
Global Catalog
is a feature of Active Directory domain controllers that allows for a domain controller to provide information on any object in the forest, regardless of whether the object is a member of the domain controller’s domain.
Get all global catalogs for the current forest
Get-NetForestCatalog
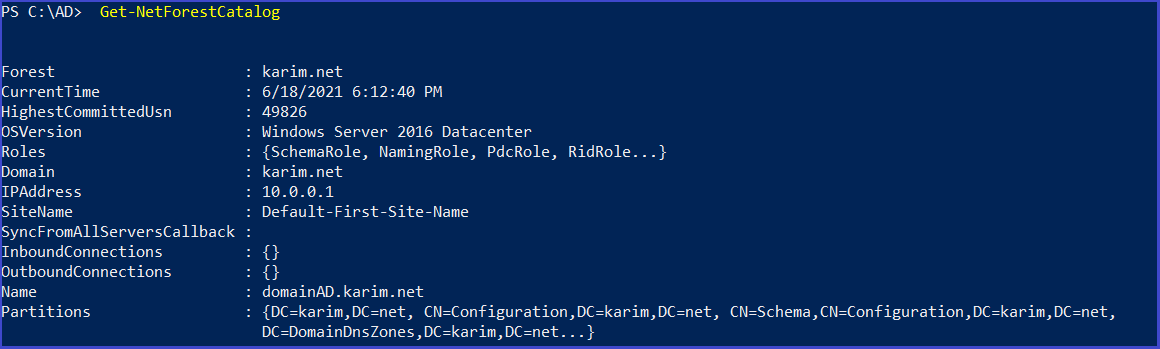
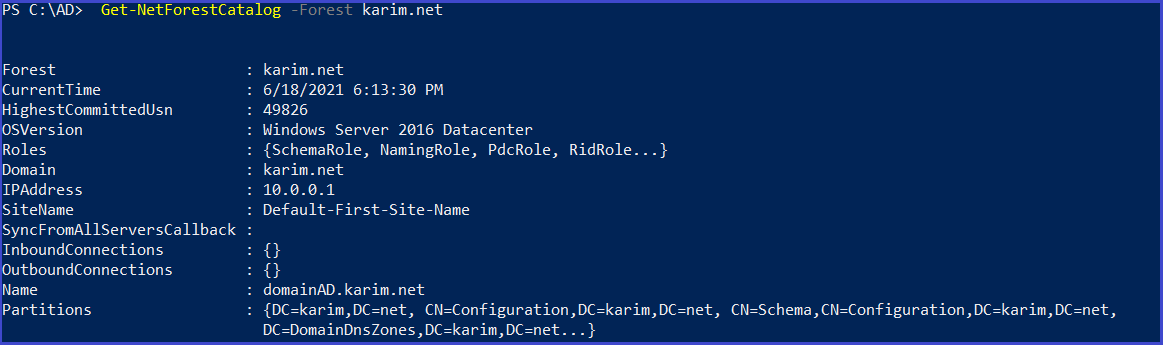
Get-NetForestCatalog -Forest <forest>
I finished part 3 today waite me in the next part.